On June 18th, 2024, thousands of car dealerships across the United States and Canada fell victim to a cyberattack against an upstream cloud service provider, resulting in widespread outages and significant operational degradation. A second attack occurred a day later and caused further damage, exacerbating an already dire situation.
What happened?
The attackers targeted CDK Global, a behemoth in the automobile SaaS industry with services extending into nearly all areas of business.
CDK Global offers SaaS solutions that help dealerships manage various aspects of their business, including vehicle acquisitions, sales, financing, insuring, repairs, and maintenance. Their services are critical for business continuity of their customers. The downstream impacts of the attack affected over 15,000 dealerships across the continental US and Canada. At this time, no direct impact to any vehicles or vehicle-connected systems has been reported.
In response to the attack, CDK shut down its IT systems, including customer logins and data center operations. At the time of this writing, three days after the initial attack, dealerships remain severely hampered by the ongoing outage, as noted in numerous X feeds:
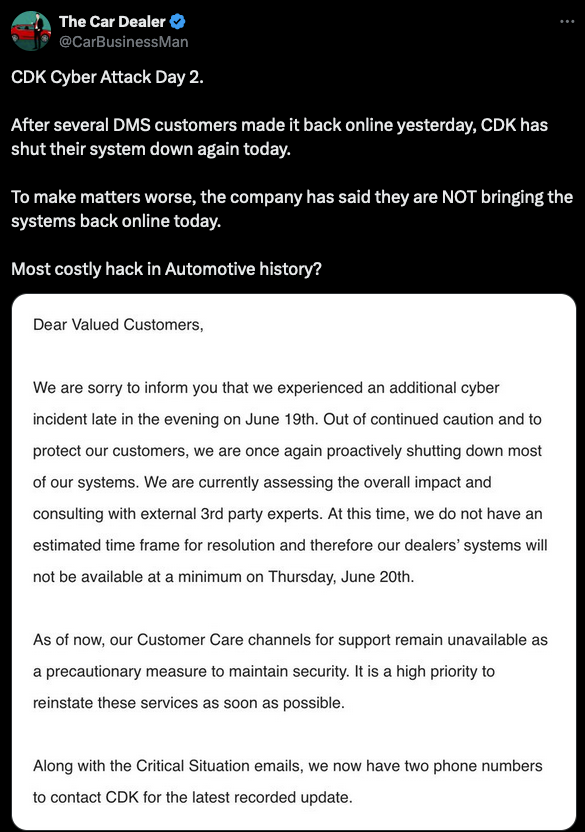
While specific impacts vary or have yet to be determined, at the time of this writing, concerns shared amongst the victims include:
- Operational Disruption: CDK’s systems were compromised, affecting dealership operations, inventory management, and customer service for an extended period.
- Reputation Damage: Public scrutiny of the breach may erode trust in dealerships and manufacturer brands, affecting customer loyalty and sales.
- Legal and Regulatory Fallout: Dealerships may face legal actions, fines, and regulatory scrutiny due to data protection violations.
- Financial Loss: Remediation costs, legal fees, and potential lawsuits can strain dealership finances.
Why were Car Dealerships Targeted?
Car dealerships pose a uniquely attractive target to malicious actors. Often lacking in dedicated security staff and formal risk management processes, they still handle large amounts of money and store vast amounts of customer data, including sensitive PII.
Also, dealership systems are often interconnected with other external systems for business processing, which may facilitate additional side channel attacks.
Recent Trends
A 2023 report by CDK highlighted that 17% of surveyed dealers experienced cyber-attacks within the past year, up from 15% the previous year. Of those dealerships affected, 46% reported negative financial or operational impacts. The scale and impact of this incident is without prescedent and may be felt for months.
Response and Recovery
To their credit, CDK Global promptly shut down affected and potentially affected systems as a precautionary measure.
- Core document management and digital retailing solutions were prioritized and later restored.
- At the time of this writing, CDK continues to conduct ongoing tests to bring other applications back online without introducing additional risk.
CDK also issued a warning to customers on its interactive voice line:
‘We are aware that bad actors are contacting our customers posing as members or affiliates of CDK trying to obtain system access. CDK associates are not contacting customers for access to their environment or systems.’
‘There is currently no known estimated time frame for resolution and therefore our dealer systems will not be available likely for several days.’
Looking Forward
It goes without saying that risk management and business continuity are critical for car dealerships. Dealerships now find themselves facing the stark reality that the two are inseparable. How they choose to move forward will shape the viability and perceived trust of the industry.
Raxis recommends that car dealerships consider the following steps when designing a robust security program:
- Data Protection Regulations:
- Become familiar with data protection laws such as the Gramm-Leach-Bliley Act (GLBA), which outlines obligations to safeguard consumers’ PII, such as names, addresses, and social security numbers.
- Implement comprehensive data protection measures, including encryption, granular access controls, and effective monitoring.
- Secure IT Infrastructure:
- Ensure dealership IT systems are secure:
- Encrypt data at rest and in transit.
- Use multi-factor authentication for identity verification.
- Regularly update software and maintain firewalls.
- Educate employees about phishing scams and secure password practices.
- Ensure dealership IT systems are secure:
- Data Integrity and Governance:
- Establish strong data governance policies and procedures:
- Conduct regular audits to identify and reconcile anomalies.
- Apply layered controls and redundancy to critical systems.
- Establish strong data governance policies and procedures:
- Limit Access and Educate Staff:
- Using the principle of least privileged access, allow access to dealership data to only what’s necessary for specific functions. This applies to personal and interconnected systems.
- Train employees to recognize security threats and respond appropriately.
- User strong, complex passwords and change them regularly.
References:
- https://www.usatoday.com/story/money/cars/2024/06/19/cdk-cyber-attack-hits-automotive-dealers/74150427007/
- https://www.ibtimes.com/cyber-attack-cripples-thousands-car-dealerships-us-canada-busy-holiday-3734785
- https://www.jmagroup.com/resources/operations/tdawa/8-important-dealership-regulations-how-to-protect-yourself-and-your-customers
- https://industrialcyber.co/vulnerabilities/check-point-finds-that-info-stealing-malware-targets-german-car-dealerships-auto-manufacturers/
- https://securityboulevard.com/2024/02/top-cyber-threats-automotive-dealerships-should-look-out-for/
- https://x.com/CarBusinessMan/status/1803722884134719894