-
2021 OWASP Top 10 Focus: Injection Attacks
By raxis-sys-admin • September 24, 2021 -
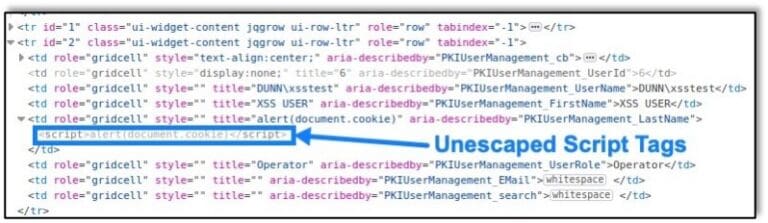
ManageEngine Key Manager Plus Cross-Site Scripting Vulnerability (CVE-2021-28382)
By raxis-sys-admin • June 11, 2021 -
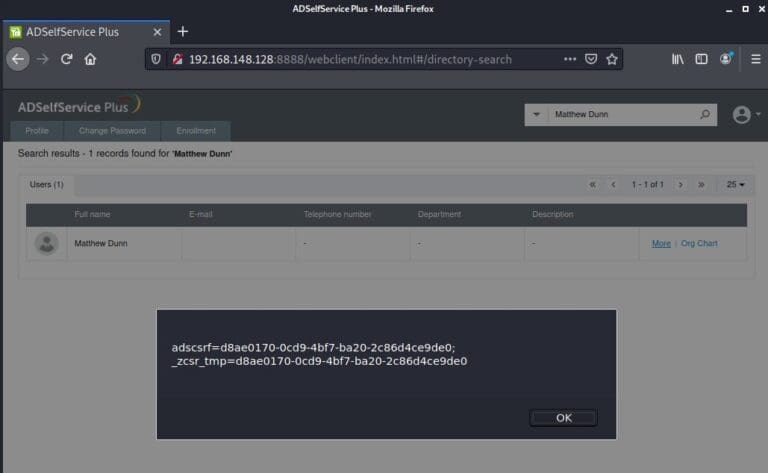
Cross-Site Scripting Vulnerability in ManageEngine AD Self Service Plus (CVE-2021-27956)
By raxis-sys-admin • May 20, 2021 -
LDAP Passback and Why We Harp on Passwords
By raxis-sys-admin • April 30, 2021 -
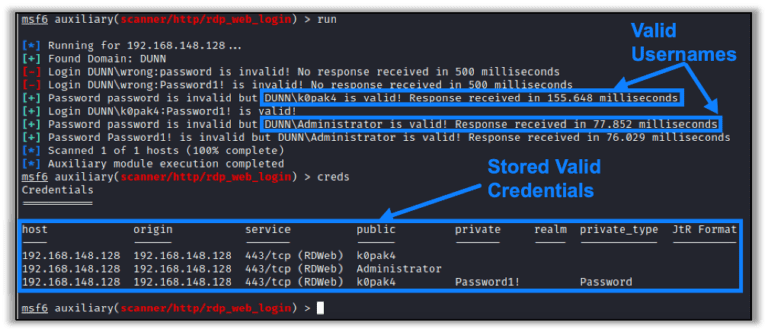
New Metasploit Module: Microsoft Remote Desktop Web Access Authentication Timing Attack
By raxis-sys-admin • February 25, 2021 -
How to Pull Off a Mousejacking Attack
By raxis-sys-admin • February 5, 2021 -
Imminent Threat for US Hospitals and Clinics, RYUK RansomwareAlert (AA20-302A) – Updated 11/2/2020
By brian • October 29, 2020 -
-
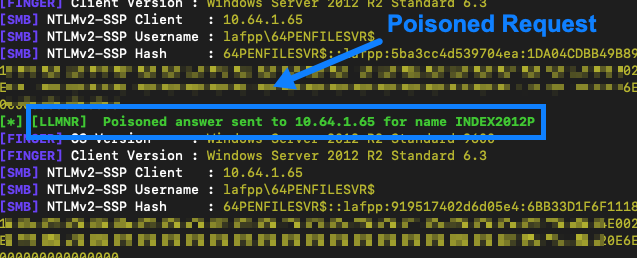
AttackTek: How to Launch a Broadcast Resolution Poisoning and SMB Relay Attack
By raxis-sys-admin • September 25, 2020 -
Understanding the Why Behind Password Management
By Bonnie Smyre • July 10, 2020 -
Here’s How Hackers Can Get Through Your Doors and Onto Your Network
By brian • June 12, 2020