-
-
-
LDAP Passback and Why We Harp on Passwords
By raxis-sys-admin • April 30, 2021 -
Remediating Account Enumeration Vulnerabilities
By raxis-sys-admin • April 9, 2021 -
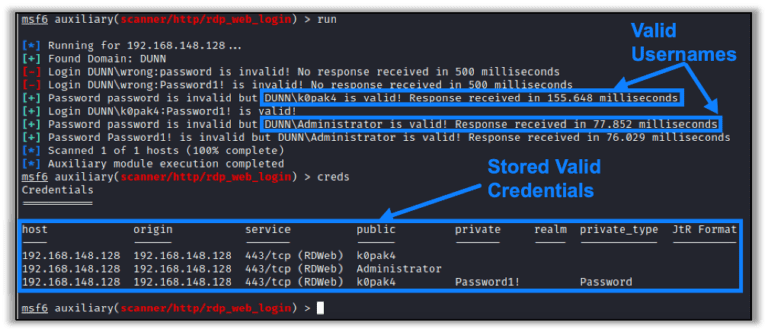
New Metasploit Module: Microsoft Remote Desktop Web Access Authentication Timing Attack
By raxis-sys-admin • February 25, 2021 -
How to Pull Off a Mousejacking Attack
By raxis-sys-admin • February 5, 2021 -
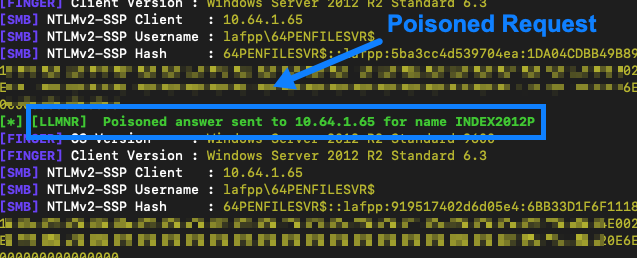
AttackTek: How to Launch a Broadcast Resolution Poisoning and SMB Relay Attack
By raxis-sys-admin • September 25, 2020 -
-
IKE VPNs Supporting Aggressive Mode
By Bonnie Smyre • May 23, 2018 -
-
The Weakest Link in the Password Hash
By brad • October 16, 2016 -
HP iLO Password Cracking
By Mark Puckett • November 28, 2014