-
Cybersecurity: It’s how to say “Yes.”
By Mark Puckett • December 31, 2024 -
Accepting Penetration Test Risks & How Compensating Controls Can Help
By tim • December 17, 2024 -
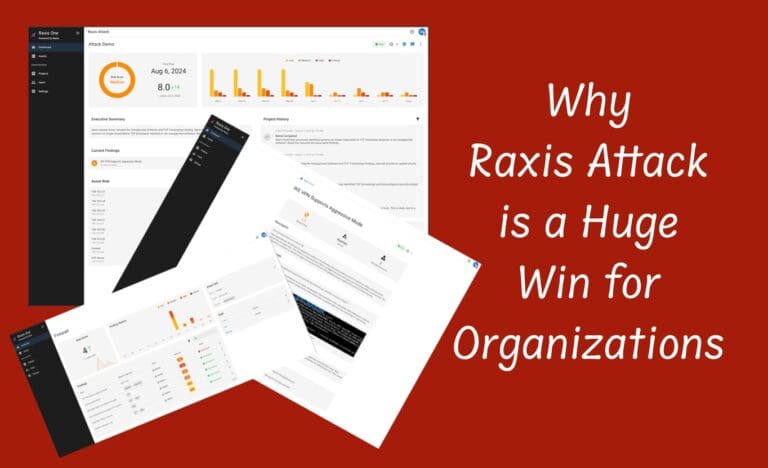
Why Raxis Attack is a Huge Win for Organizations
By ckelly • October 22, 2024 -
The CrowdStrike Outage: Lessons Learned
By Scottie Cole • July 25, 2024 -
Ongoing Cyber Attack Disrupts Car Dealerships
By brian • June 21, 2024 -
Password Length: More than Just a Question of Compliance
By brian • June 4, 2024 -
SOC 2 Compliance: Is it Right for Your Organization?
By Bonnie Smyre • May 21, 2024 -
Raxis Achieves SOC 2 Type 2 Compliance
By Mark Puckett • May 14, 2024 -
What to Expect with a Raxis Wireless Penetration Test
By Scottie Cole • September 6, 2022 -
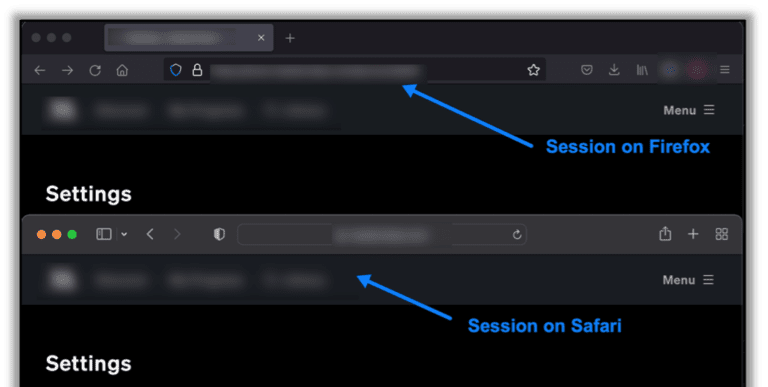
Why We Take Simultaneous Sessions Seriously
By raxis-sys-admin • April 8, 2022 -
CIS vs. NIST: Understanding Cybersecurity Standards and Frameworks
By brian • January 7, 2022 -
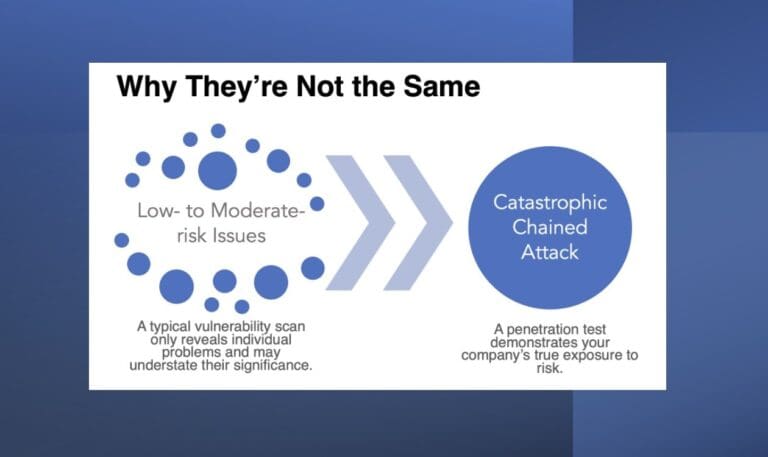
Chained Attacks and How a Scan Can Leave You Vulnerable
By tim • December 10, 2021