Gone are the days of Nigerian princes who left you their fortune. Today it’s much more difficult to separate the genuine emails from the malicious ones that are out to steal your information and your money. While many of us deal with the spam that ends up in our personal email inboxes, Raxis helps many companies avoid corporate and customer information leakage from phishing emails targeted at unsuspecting employees.
Identify
Knowing how to identify suspicious emails is the first step in protecting your information as well as that of your employer and customers. I’ve performed many phishing campaigns for our customers, and I’ve heard multiple stories of smart, conscientious employees falling for clever phishing campaigns. The fallout, including public relations pitfalls, can be large enough that IT budgets get redirected to secure the environment and regain customer trust.I always tell our customers that it doesn’t hurt anyone to take a little extra time to react to an email. When I run phishing campaigns for our customers, I like to send the email out at the start of the day or at the end of the lunch hour. At these times most of us don’t want to be bothered by a new email request. We have work to do, and we’re focusing on getting to it and accomplishing our goals for the day.I make sure the tasks in the phishing emails are quick, simple, and easy to finish:
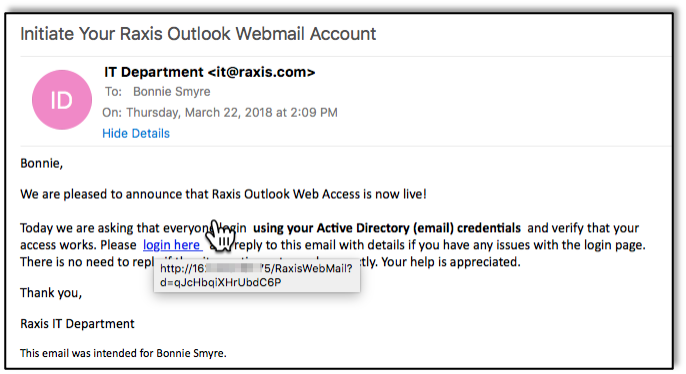
“Just in time for the holidays, we’ve implemented web mail so that you can be home with your family and still answer emails! Your account will only activate if you log in at the following URL by the end of the day!”
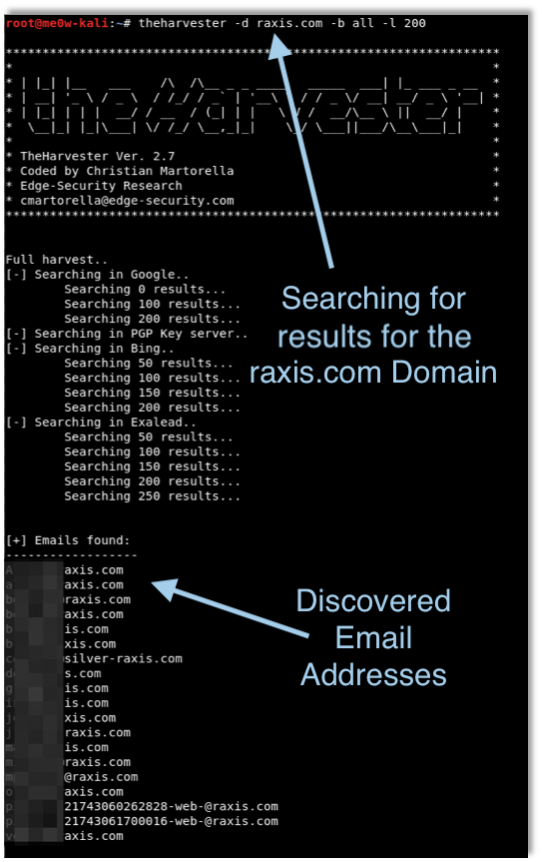
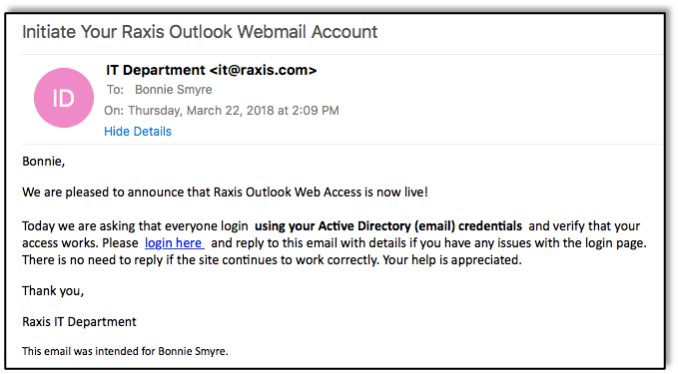
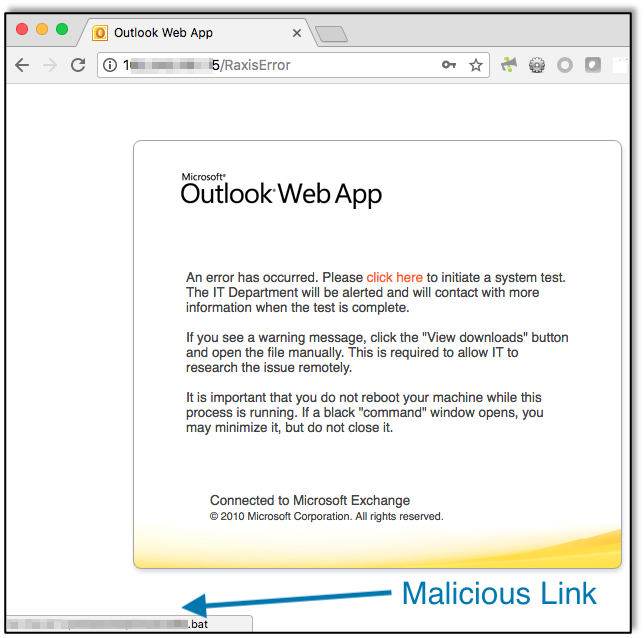
Well, maybe your IT department wouldn’t be quite so excited, but you get the idea.Phishers know common systems that most businesses use, and it’s often easy to find sample login pages online. Several free and paid tools exist that help companies perform phishing tests… and that help phishers steal your data as well. For this article, I spent about ten minutes finding email addresses and creating an email and website to steal credentials from my fellow Raxis employees. Just ten minutes, then I sit back and see if anyone responds.Step one was to find email addresses. Sound difficult? You’d be surprised. Search engines such as Google or Bing are a huge help, and social media sites, such as LinkedIn, provide employee names even when they’re not your connections.Manually searching for email addresses was taking too long, so I logged into my Kali Linux box and fired up theHarvester. In less than a minute, I had the full list of Raxis email addresses pulled from various search engines. There are also free tools that allow attackers to discover the format of a company’s emails, such as “[email protected],” so that I can create my own mailing list if I know some employee names.Now that I have a list of email addresses, I need those folks to give me their login information. There are tons of great tools that make it easy for users to set up a phishing campaign in minutes, such as the open source Social-Engineer Toolkit. This time I use Rapid7’s Metasploit Pro phishing tool.I start with a simple email. In some cases, I research the company’s culture and target a campaign at specific employees, but most of the time I can good results by setting up a generic campaign that does not require me to know a lot about the company. In this case, I pick an Outlook Web App (OWA) site and hope that employees find it familiar enough to fall for my story without looking too closely. Using the phishing tool, I add a number of features that make the email look legitimate, such as using a fake raxis.com email address and including the recipient’s name. Think about it: if I found your email address, I likely know your name, but it still looks official to add it to the email.If the recipient clicks the link in the email, they are taken to a page that appears to be a legitimate OWA webpage. If they enter their login information and click submit, they move onto an error page that I built. It tells the recipient that there was an error, and all they need to do to resolve it is click on a handy link that can do the fix for them while they continue with their work. Unfortunately for anyone who clicks on the link, a malicious file meant to open a remote session to the user’s computer will be downloaded, effectively giving me background access to that machine and potentially the network where it is located.
React
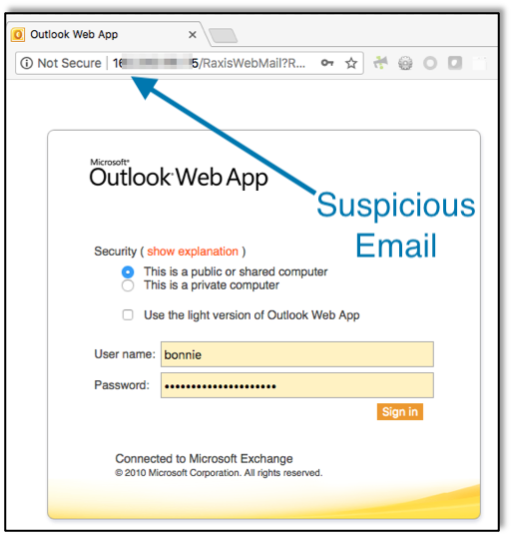
This is scary stuff, but the real question is: “What can I do about it?”First, there are some clues in the email itself. When I hover over the link, I see that the URL starts with “http://” instead of “https://.” A real OWA webpage would almost certainly use an encrypted “https” connection. The site also doesn’t have the company name in the domain: it’s just an IP address. That’s a big red flag as well. However, many phishers know that vigilant employees will look for these issues, and configure the malicious website to use an encrypted connection, and register a domain name that might trick employees if they don’t look closely, such as “https://rax1s.com” or “https://raxls.com.” Make sure you look closely at the link!If you find an email strange or unexpected in any way, ask about it. Most companies are concerned with phishing and would much prefer that you ask IT if an email is real rather than clicking on the link. Some companies have phone numbers, email addresses or websites that allow you to report a suspicious email. If not, give your IT helpdesk a call or forward the email to them asking them to check. Have you ever received an email from IT notifying you that you may have received a phishing email and asking you to delete it? Someone likely reported it in time for IT to nip it in the bud, thwarting the attacker.What if you clicked on the link in the email and then became suspicious of the website? This is dangerous, as webpages are far more likely than emails to host malicious files that may not be caught by company controls. Immediately report the email and the fact that you clicked on the link to your IT department. They will likely be grateful that you told them quickly so that they can check for and mitigate any threat. Never enter credentials or other private information on a suspicious website until you get the official go ahead. In past customer phishing campaigns, I have listed my phone number on the website saying that they can call to confirm that the site is legitimate. Never trust the email or the webpage! Contact your IT department in ways that you know internally before trusting the site. If you call the phisher during a phishing campaign, they will definitely confirm that you should enter your credentials on the site!
Next Steps If You Fall for the PHISH
So what happens next if you entered your credentials, or even clicked on the malicious link on the error page?
Step 1: Report the Phish and Your Actions
First of all, I’ll repeat it again, contact your IT department. They may have a process, and they need to get started as soon as possible. The sooner you tell them, they more able they will be to contain the threat.
Step 2: Change Your Password
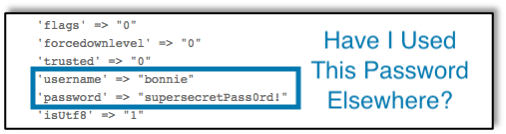
Next change your password. Change your password on every system, company or personal, that uses that password. Attackers love to try credentials in any place that they have access. They might login to your email account and delete the email that IT sends telling you what to do next, or they might email a customer to scam them from your account. Changing your password as quickly as possible helps contain the threat. Here’s another handy post written by one of my colleagues with tips about creating a strong password: https://raxis.com/the-weakest-link-in-the-password-hash/
Step 3: Reboot Your Computer
Finally, reboot your computer. If you clicked on the malicious link in the error page that I created, a reboot would break my remote session to your computer. This doesn’t always work, but it also doesn’t hurt. Let your IT department know exactly what saw and what you did. In a case like this, they will want to look at your computer and make sure they remove any threat. That may seem like a lot of work, but it also sounds a lot better than someone watching you through your computer’s webcam or using your computer to attack other machines on the network. Once they have access, the attacker likely no longer needs your password even for extended access. It’s always best to report the issue to be sure.
Want to learn more? Take a look at the next part of our Social Engineering discussion.

Leave a Reply