
Raxis Strike
Tailored Penetration Testing for Unparalleled Security
Raxis Strike: Tailored, Thorough, Trusted
Raxis Strike represents the pinnacle of Traditional Penetration Testing, offering a collaborative and tailored approach to cybersecurity that evolves with your threat landscape.

Real Exploitation
By leveraging actual hacker-created exploits and techniques, we offer invaluable insights into potential attack vectors and their impact, enabling you to fortify your defenses against real-world threats effectively.

Pivot and Escalate
The Raxis storyboard meticulously details how our penetration testing experts simulate sophisticated insider threats, demonstrating the potential path of system compromise and privilege escalation.

The Power of Team
The Raxis team of expert penetration testers frequently work together to combine their diverse skills and expertise to evaluate any technology or software, delivering optimal security testing for your unique infrastructure.

Industry Specific
Industry-specific expertise allows the Raxis team of penetration testers to efficiently target sector-unique vulnerabilities and compliance needs, ensuring more effective security assessments.
Key Features of Raxis Strike
Raxis Strike is our traditional penetration testing service provides the insights you need to make informed decisions about your cybersecurity strategy.
Collaborative Penetration Testing Engineers
Our expert team collaborates internally and with you to combine skills as needed to simulate sophisticated cyber attacks, tailoring our approach to effectively assess diverse technologies. This comprehensive approach delivers invaluable, actionable intelligence to strengthen your security posture.
Customized Testing Scenarios
Every organization faces unique security challenges. Our penetration tests are tailored to your specific digital environment and industry, ensuring relevance and maximum effectiveness.
Data Exfiltration Demonstration
Unlike many competitors, we include this crucial step to showcase the real risks stemming from cybersecurity vulnerabilities. Not only is this the fun part of our jobs, but also it drives improvements to cybersecurity budgets.
Compliance Support
Raxis Penetration Tests fulfill various compliance mandates, ensuring you meet or exceed regulatory requirements. Raxis routinely performs Penetration Testing for NIST 800-171/CMMC, PCI, HIPAA, GLBA, ISO 27001, and SOX.
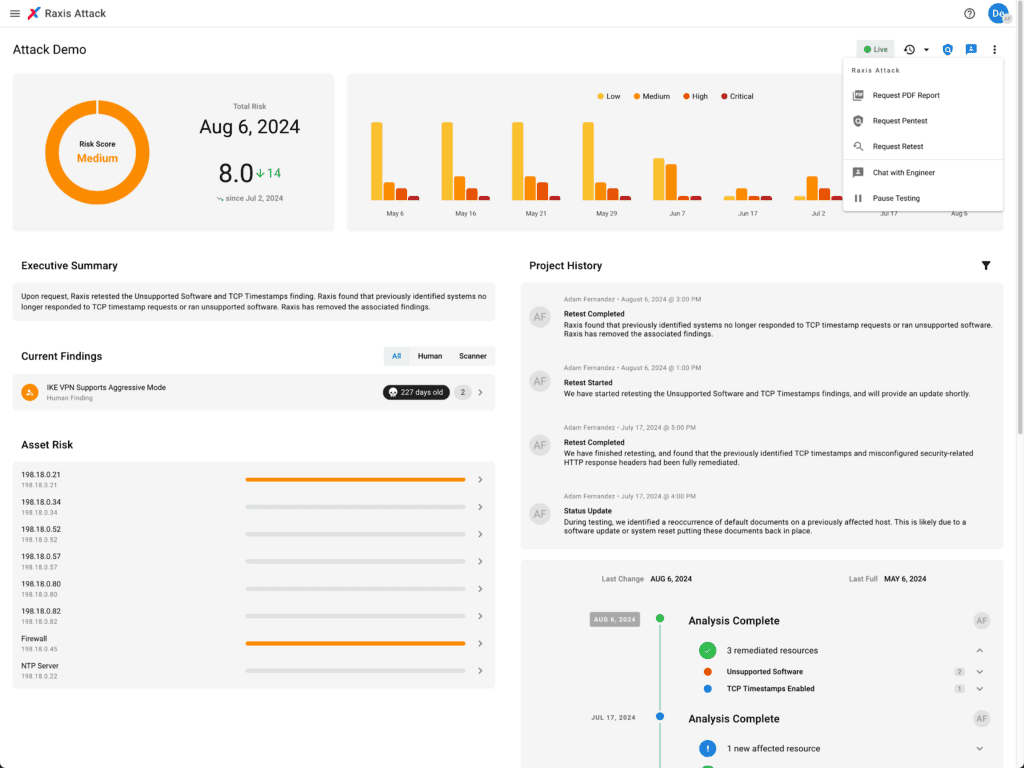
You’re In Control With Raxis One
Use Raxis One, our internally developed console for Penetration Testing, to view the latest details on your attack surface in real time, prioritize remediation, and easily retest.
Cybersecurity Meltdown Averted
Raxis Hack Stories
Our stories are based on real events encountered by Raxis engineers; however, some details have been altered or omitted to protect our customers’ identities.
In the high-stakes world of cybersecurity, the Raxis Strike Team uncovered a chilling vulnerability that sent shockwaves through the industry. During a routine assessment, our team stumbled upon an embedded device controlling a nuclear reactor—a discovery that made their hearts race. But what truly alarmed them was not just the device’s critical function but its startlingly lax security.
The device was accessible via telnet, an outdated and notoriously insecure protocol. Even more alarming, it was protected by nothing more than default credentials—a digital equivalent of leaving the keys in the ignition of a nuclear-powered vehicle.
Recognizing the gravity of the situation, Raxis experts immediately alerted the client, demonstrating not just technical prowess but also a deep commitment to responsible disclosure and client safety. This incident serves as a stark reminder that, in the complex landscape of modern networks, even the most critical systems can harbor overlooked vulnerabilities. Raxis’ ability to identify and address such high-stakes issues showcases why our penetration testing services are crucial for organizations seeking to fortify their defenses against potential catastrophic breaches.
The Raxis Strike Process
Raxis has been a leader in cybersecurity for over a decade, providing our acclaimed Traditional Penetration Testing service to organizations of all sizes. We adhere to the industry-standard MITRE ATT&CK framework, employing a proven methodology that consistently delivers comprehensive security assessments. This approach enables organizations to identify and mitigate critical vulnerabilities before malicious actors can exploit them.
Our process, from the client’s perspective, is outlined below:
- Scoping: We work closely with you to define the scope of the penetration test, ensuring it aligns with your specific needs and objectives.
- Vulnerability Identification: We uncover and document all vulnerabilities found during the testing process.
- Attack Simulation: Our team works together to safely use advanced hacking tools and methods to simulate real-world cyber attacks on your systems.
- Exploitation: Within your parameters, we demonstrate the potential impact of any identified vulnerabilities through controlled exploitation and data exfiltration.
- Reporting: You receive a comprehensive report detailing our findings, including a detailed storyboard and prioritized remediation recommendations.
- Debrief: Our experts walk you through the results, answering questions and providing guidance on addressing vulnerabilities.
- Retest: If applicable, we will perform a retest of any items found to verify that the security risk is no longer viable.
F.A.Q.
Frequently Asked Questions
What is Raxis Strike?
How does Raxis Strike differ from automated vulnerability scans?
What types of systems can Raxis Strike test?
How long does a Raxis Strike penetration test take?
What does the Raxis Strike process involve?
How does Raxis ensure the safety of my systems during testing?
What kind of report will I receive after a Raxis Strike assessment?
Does Raxis Strike include retesting after vulnerabilities are addressed?
Yes, Raxis can include a retest to validate remediation efforts, which is often required for compliance purposes.
