I’m Bonnie Smyre, Raxis’ Chief Operating Officer, back with the second in our two-part feature about how to hire a penetration testing firm. This time, we’re suggesting some questions to ask and answers to listen for in the selection process.

In the first article on this topic, I focused on the six things you and your company should do to begin your search for a pentesting firm. We discussed the importance of identifying why you need a pentest, understanding the data and systems that are at risk, figuring out what type of tests you need, consulting with trusted advisors, as well as checking ratings, reviews, and references.
If you followed those steps, you’re well-prepared to begin your interviews with prospective firms. Toward that end, here are some questions you should ask during your conversations and some key points you should be listening for in the answers.
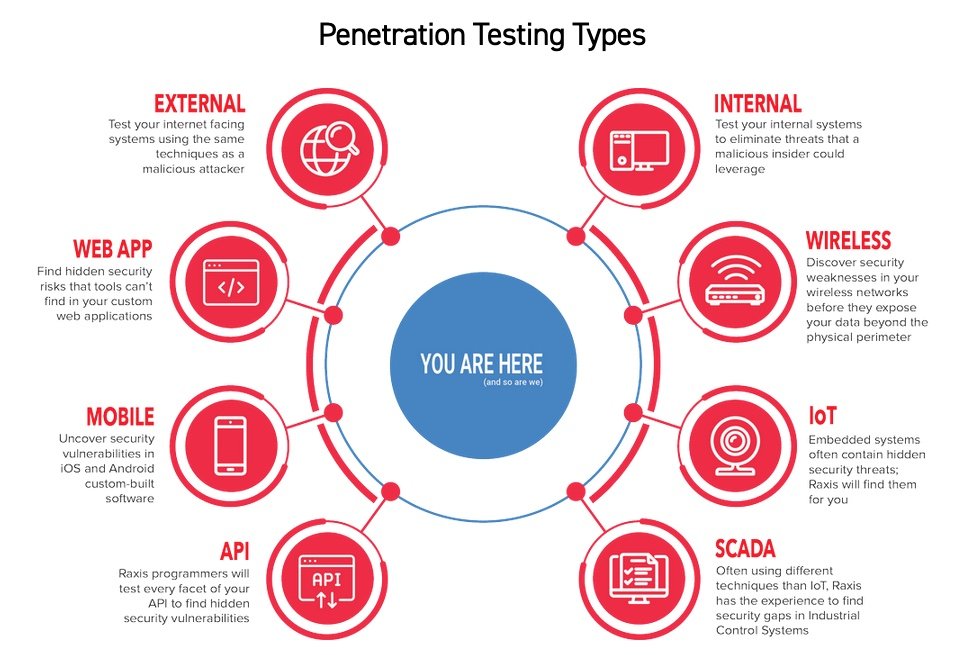
Question 1: What is your experience in performing the type of penetration testing our company is looking for?
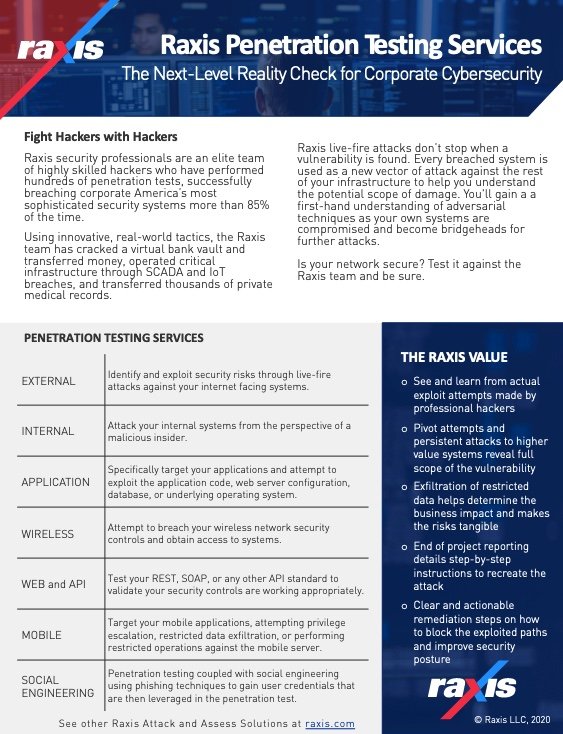
At Raxis, we’re happy to tell you how many and what kind of tests we’ve done and share with you some of our most common findings. If we don’t think the pentest you’re shopping for is going to accomplish your goals, we’ll tell you why and recommend a different type of engagement that will. That’s part of our job as professionals, and we have found that it makes for a better customer experience and often saves time and money.
On the other hand, if the firm you’re interviewing continually tries to steer you toward more expensive testing or something far different than you think you need, that can be a big red flag. They may be trying to upsell you, or they may simply not have the expertise to conduct it.
A point we make frequently is that vulnerability scanning is not the same as penetration testing. So, also beware of firms that try to downplay your needs and tell you one is as good as the other. Raxis might recommend a vulnerability scan, but we will never tell you that it should supplant a genuine pentest.
Question 2: Tell me about your experience in my industry?
Obviously similar to question 1, this one is based on your reasons for doing a penetration test. If your business is regulated and subject to special laws, rules, or industry requirements, you’ll save a lot of time with pentesters who are familiar with them. For example, if your company takes electronic payments, Raxis knows the Payment Card Industry Data Security Standards (PCI-DSS), and we can plan our testing to make sure you’re compliant.
When you ask this question, listen to see if the pentesting company proactively mentions any applicable regulations in your field – such as HIPAA compliance for health care organizations or FINRA, GLBA, or SOX, for financial institutions. If they don’t, ask and make sure they understand your needs so that you don’t have to pay for more testing later.
Question 3: How comprehensive is your reporting?
The goal of penetration testing should be to give your team actionable results that enable them to prioritize issues and begin resolving them in order of severity. Ask potential pentesting firms to provide a sample report. Does it summarize the issues for executives? Does it categorize the findings effectively and provide sufficient detail for your team members?
Raxis includes storyboards so that your team can see exactly what we did and how. We also exfiltrate and redact sensitive data when we can. That’s powerful proof of what bad guys can do if your network isn’t secured.
Also, be sure to ask whether they report where your defenses were solid. This can be especially important when you’re building a cybersecurity budget. Many Raxis clients have found it helpful to show their leadership examples of where previous security enhancements are working well. (And it shows you that those defenses were in fact checked.)
Question 4: Who are the people I’ll be dealing with? What are their qualifications?
Be sure that the companies you interview can identify the person who will serve as your point of contact throughout the testing, to work with you on scheduling or to quickly resolve problems that can cost precious time.
The company should also be willing to tell you about the experience and certifications of team members. It’s a good idea to ask whether the team that conducts your test will include members with similar qualifications so you know it’s not a bait-and-switch.
At Raxis, the diverse skillsets our team members bring to the table are one of our greatest strengths and something we like to talk about. Before they became penetration testers, our people were corporate cybersecurity leaders, software engineers, web developers, and network admins. And they also bring to the table computer hardware, electronics, mechanical, and IoT experience.
Question 5: How much will it cost and why?
Raxis’ CEO Mark Puckett addressed pentest pricing in a recent blog post that goes into detail about the factors that can and should drive the cost of a high-quality penetration test. In summary, the scope of the testing, the time it will take, and the skills of the testers are all cost drivers.
If the firm mentions additional services they provide, be sure to ask if those are covered in the cost you’ve been quoted, or if there is an additional fee. And ask if there is a minimum engagement time.
Minimums are common in the industry. Raxis requires three days, but we’ve seen other companies with seven to 10-day minimums. Make sure you ask this early in the conversation. Otherwise, you could waste time you don’t have being sold services you don’t need.
Conclusion
Hiring the right penetration testing firm necessarily involves a lot of research and careful consideration. After all, you need a company that can bring to bear all the skills, determination, and devious creativity of black hat hackers – and still act as your trusted security advisor, providing actionable reporting on your vulnerabilities.
The preparation outlined in part one, along with the questions above, should help you find the best match for your specific needs.
Of course, we hope you choose Raxis, and we’re ready to put you in touch with our experts whenever you’re ready to talk.
Want to learn more? Take a look at the first part in our How to Hire a Penetration Testing Firm Series.