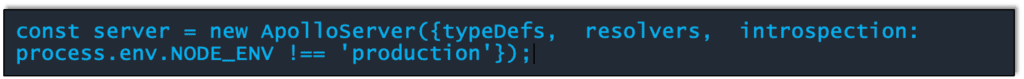
“Brice noted the different ways that students could get into cybersecurity and pointed out that students need to put in work to qualify for jobs and explained the certification process and how to determine which certifications are valuable to possible employers.”
Georgia’s Putnam County School District takes cybersecurity seriously — not only as an administrative safeguard, but also as an important new skillset to teach the next generation. Regardless of their ultimate career choices, today’s students will be tomorrow’s workforce and cybersecurity will be a critical component of every job.
It was in that context that Ed Ozols, a computer science and cybersecurity teacher at Putnam County High School invited Raxis lead penetration tester Brice Jager to speak to his students about the role of pentesting and how it keeps networks safe.
Some Words from Ed:
Brice was a great help to my cybersecurity class. This is the first time that Putnam County High School has offered cybersecurity and we will be providing the full pathway that ends with a certification exam to our students. We are one of the few districts in Georgia that offers the full pathway. Brice spoke with students who are taking their first cyber class. He was able to outline what life was like for a cybersecurity specialist (in his case, as a pen tester).
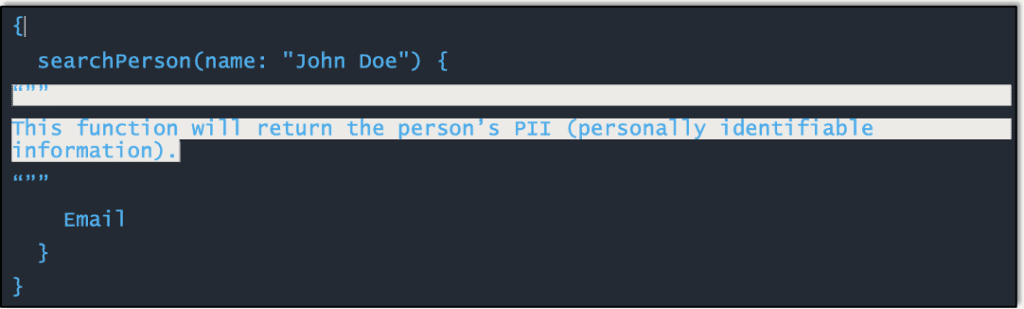
Brice noted the different ways that students could get into cybersecurity and pointed out that students need to put in work to qualify for jobs and explained the certification process and how to determine which certifications are valuable to possible employers.
The students had numerous questions that Brice answered for us, and his explanations were understandable to my students who have just begun to get their toes wet in cybersecurity and do not have a depth of cybersecurity knowledge.
They were glad to hear from him. One student, who is normally shy, came up to me and talked with me about a future in cybersecurity. I have other students who plan on pursuing a career in cyber and this helped cement those plans.
I am helping develop the future of cybersecurity and Brice was an important part of this development in the students that he was talking to. My students and I thank you for connecting us with Brice. It is two weeks after his discussion and my students are still relating things that he said with the concepts I am teaching in my class (as in “Brice said…”).

Georgia’s Putnam County School District takes cybersecurity seriously — not only as an administrative safeguard, but also as an important new skillset to teach the next generation. Regardless of their ultimate career choices, today’s students will be tomorrow’s workforce and cybersecurity will be a critical component of every job.
According to Brice, the experience was very rewarding for him as well.
“I’ve been an instructor in some of my previous jobs, so it feels natural to ease back into that role,” he said. “What made this experience unique is that I had an opportunity to introduce young people to the field of penetration testing and, I hope, sparked a deeper interest in cybersecurity among them. It’s rewarding to think that one or more of those students could decide on a career in cybersecurity because of this introduction.”