“Like it or not, all of us are on the front lines in a cyberwar that is heating up with every day that passes.”
Bonnie Smyre, Raxis Chief Operating Officer
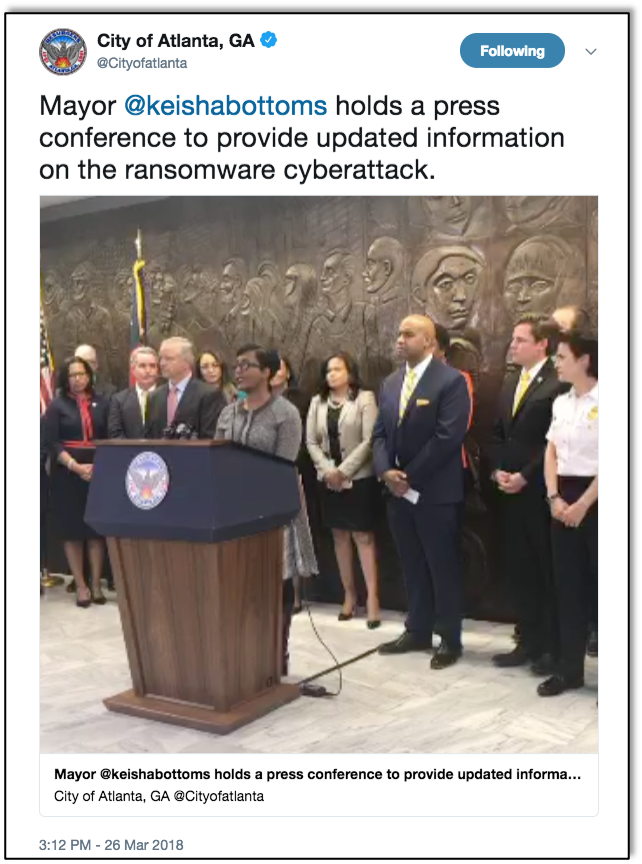
In the wake of the Colonial Pipeline breach, security analysts have discussed the idea that direct retribution might be an effective deterrent to the large-scale cyberattacks of the sort the US is experiencing ever more frequently nowadays. As someone with a strong background in Russian and Eastern European studies, I understand the historical precedent that drives this mindset. However, as a cybersecurity professional, I know that half-century-old strategy will not be nearly as effective against the challenges we face today.
Some ‘MAD’ Background
In the most dangerous days of the Cold War, US and Soviet leaders agreed to a counterintuitive policy that helped ensure neither side would launch a catastrophic nuclear first strike. Recognizing that stockpiles of atomic weapons were sufficient to destroy Earth many times over, the two superpowers agreed that the world was most secure when both sides maintained the ability to respond to a first strike with an equally devastating counterstrike.
Though it sounds barbaric, the strategy of mutual assured destruction (MAD) was one reason a period of détente lasted long enough for both nations to de-escalate tensions and negotiate dramatic reductions in the size of their nuclear arsenals.
The New Battlespace
Though the Soviet Union fell apart in the early 1990s, and the US ‘normalized’ relations with China, the threat they posed to America never disappeared completely. Instead, it has evolved with new technology and shifted into cyberspace. Hackers with ties to Russia and China are widely believed to have been responsible for high-profile breaches of government agencies and contractors, meddling in US political campaigns, and sabotaging critical infrastructure.
I say ‘widely believed’ because in the shadowy world of hackers it’s nearly impossible to prove an attack was state-sponsored. Malicious actors are very much cybercriminals without borders, and it’s not hard for hostile nations to contract out some of their dirtiest work.
As for the weaponry, ransomware, like the type used in the Colonial Pipeline hack, can be a few lines of code, readily available for sale on the dark web. Some of the more helpful black hats even offer support for an additional fee.
Where Deterrence Fails
The simplicity and anonymity of cyberwarfare do more than give cover to state-sponsored actors. In the context of mutual assured destruction, a more dangerous possibility is that non-state actors could launch an attack that triggers a misdirected, full-scale state response. In that scenario, it’s easy to envision a rapid escalation leading to military action.
An even bigger problem with the MAD concept, however, is its central tenet that the civilian population is purposely left exposed. In the case of nuclear war, there is a macabre logic behind that. Taking away the fallout shelters, civil defense infrastructure, and air raid drills made clear to everyone that a nuclear war between the superpowers would likely be the end of civilization. Entering the launch codes meant worldwide annihilation, plain and simple.
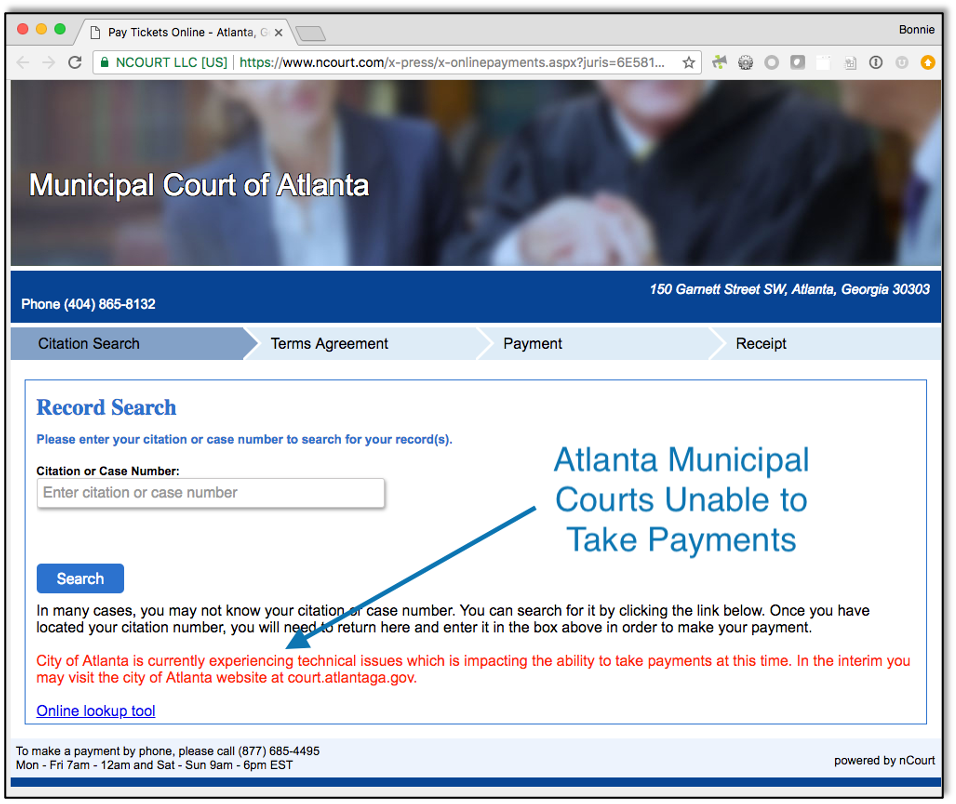
In the case of cyberwarfare, there simply isn’t a clear delineation between military and civilian or even public and private sector targets. Colonial is a private company, as are many utilities and other organizations that are of vital importance to our national security. Was the recent ransomware attack a simple economic crime or a strategic strike on the Eastern Seaboard?
Nor is there a foolproof way to gauge the severity of the attack. A small business might be hacked in order to reach a larger upstream supplier. And disrupting several municipalities could have the same strategic impact as an attack on the federal government.
We are the Front Line
From a practical perspective, what all this means is that, at most, deterrence can only be one part of a much larger strategy. And, unlike the Cold War, this new state of perpetual, persistent cyberwarfare can’t be waged solely by our military or managed by diplomats alone.
We’re all in this together. As long as one business is at risk, all of our businesses are. If our businesses are at risk, so is our government. And if our government is at risk, so are our people – from all walks of life.
Like it or not, all of us are on the front lines in a cyberwar that is heating up with every day that passes. The good news is that there are things we can do to protect ourselves and to become harder targets. As we do so, we raise the technological barriers, drive up the costs, and increase the risk to those who would attack us.
Mutual assured destruction helped end the Cold War without nuclear confrontation. But the key to ending global cyberwarfare may well be mutual cooperation – among our government, our military, and our businesses of all sizes.