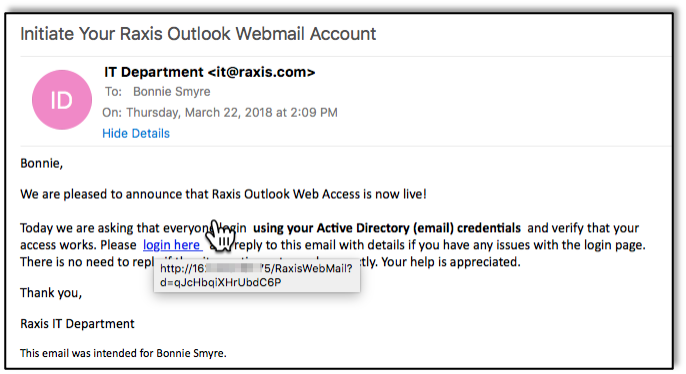
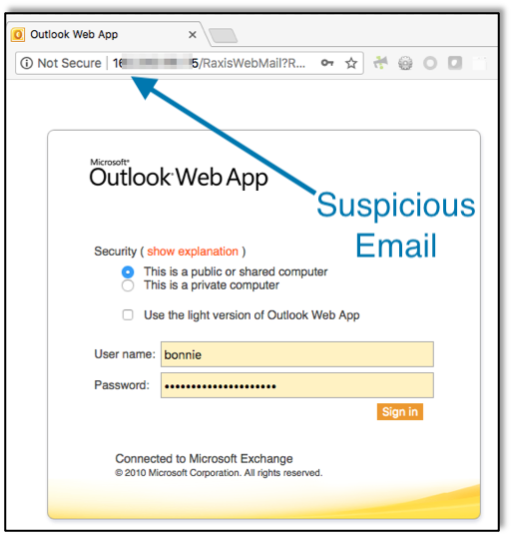
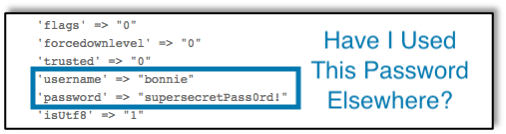
In Part 1 and Part 2 of this series, we discussed remote social engineering that an attacker could perform from any location. Those types of attacks rarely are traced back to the attacker who could be located anywhere. The social engineering attack that we’re discussing in this post is much more brazen. In this case the social engineer is actually located onsite, possibly talking with you face-to-face.The stories below are all from ethical physical social engineering engagements that my colleagues and I have performed. Our goal was to help each company find weaknesses so that they could correct them and educate their employees to make the job site more secure. My goal in writing this post is the same. As with all social engineering attack vectors, education is the best defense. For that reason, I’m focusing this post on the interpersonal aspects of SE. Some of my colleagues at Raxis made a video last year explaining some of the technology that can be used on physical SE engagements. Check it out at https://raxis.com/2017-04-19-physical-security-pitfalls/ to learn more about that.
Getting In
Companies often put safeguards in place to secure entrances and then hope that the bad guys stay out. Surprisingly, getting in is often much easier than you might expect. I have used platters of cookies and cakes to gain access on some engagements, but often it’s even easier than that.I once was attempting to enter an office building located in the suburbs of a large city and scoped out the building on the Sunday afternoon before the engagement started. I find this to be a good way to find out about the building and security policies in place so that I can make a plan before the Monday morning rush. Also, different security guards are often on duty on the weekends, meaning I likely won’t be recognized the next day when I start the engagement. In this case, a colleague and I checked out the building and discovered that all doors except the main entrance were locked. The main entrance was open during posted hours, and a uniformed security guard was visible behind glass windows. We decided that tailgating during the morning rush was our best option. The next day we arrived and immediately split up. After a few attempts, I saw a woman heading towards a door I was near. I looked upset & riffled through my purse frantically. When she walked up, I told her I couldn’t find my badge anywhere and could she let me in. She was definitely suspicious. “What department do you work in?” I told her IT, a department that is likely to have employees in or to need access to several buildings. She let me in and told me that it was okay because I worked for IT. And then she told me that she disliked the rule that they could not let people in, and IT made that rule, so I had better not tell my coworkers. Once in the building, I plugged a device into a network port in an open cube and called my colleague so that he could begin remote access to the network.I could tell multiple stories of people holding doors for me, especially during busy times of day — morning, lunch, and at the end of the day. On one engagement I was attempting to clone badges and eventually wondered why since every single person who passed me as I obnoxiously stood outside a locked door held the door for me. When you realize that many companies rely on locked doors for security, this starts to become scary.So how about another story that is much the same, but possibly not as expected. On an engagement in the financial district of New York City a few years ago, I had more hurdles to make my way into the office. The large skyscraper I was in had two elevator banks. Each bank had turnstiles that required employee or visitor card access. Two guards were seated at a security desk that had a clear view of both elevator banks. Once I made it to the elevator, I knew a floor number but did not know what security measures were in place. I stood near a snack shop and watched as most people used the elevator bank for the floors I didn’t need. When I eventually saw someone head to my elevator bank, I casually, but closely, followed. No alarm. Later testing showed me that the alarm would go off if I allowed a comfortable distance between myself and the person I was tailgating but the turnstile would still work as long as I followed someone through. I followed my target onto an elevator and discovered that she was going to the floor I needed. She used her card to allow the elevator to go to that floor and then used her card to get into the office area of the floor. Though the floor was designed to lock visitors in the elevator area where they used a phone to request access, my target held the door open for me. Once I was on the floor, I sat in the break room, walked around work areas and file cabinets, and, fifteen minutes in, eventually had to start acting suspicious before anyone asked me who I was and what I was doing. The safeguards in place made everyone believe that they floor was secure and that everyone there must have been fully vetted.
Staying In
It’s definitely a win to say that we got into our customer’s building. The test, though, is to see how we can exploit that, and, unless we know exactly what we are looking for, that requires staying in the building for an extended period of time without getting caught. Finding our way around takes a while. I’ll take photos of fire exit maps and then run into restroom to have time to look them over and figure where to go next. Most of the time we’re entering buildings blind and figuring out where to go as we go.Remember that suburban office building I mentioned above? My colleague and I went back at 5pm. We bought coffee at a local spot across the street and stood outside a locked door drinking that local coffee. The first person who walked out the door held it for us. We walked in and walked past rooms labeled with department names. When we found one with no name, we walked in and saw that it housed offices and cubes that appeared to no longer be used. We waited inside an office there for an hour. When we left our hiding space around 6pm, the building was deserted except for the cleaning crew. We ran into the same members of the cleaning crew multiple times, and they never stopped us or reported us. Earlier in the day we had gathered some credentials in a phishing campaign. We were able to use those credentials to login on a customer service representative’s PC and to view customer financial and medical information. We had full access because internal doors were left unlocked after hours and the only employees we met did not report us.Another time I was in a large hospital. As you’d expect, at a hospital, it wasn’t hard to gain access. There were nurses and doctors all around, though, and the computer access and private documents that were my aim, were all behind nurses stations. Luckily I had guessed this might be the case and had bought a cheap pair of scrubs before starting the job. I wore the scrubs along with a lanyard that had a blank white card on it, and I gained full access. To what?
- Computers
- Papers on printers and fax machines
- Medical files and binders with patient information
I took my time and went from floor to floor. I was not stopped or questioned even one time. In fact, I made a friend in the elevator as I was leaving the building. We chatted about how being a nurse hurts your feet after running around all day. I later found out that the scrubs I was wearing were a color not even used at that hospital.So timing helps and dressing the part helps. One last story on this topic. Back to that skyscraper in NYC. On one occasion there I was tailgating with the lunch crowd to a different floor using the popular elevator bank. I slid through the turnstile following someone but wasn’t quite fast enough. The alarm went off, and a security guard started walking towards me. Just then an elevator opened, and I walked in with the crowd. On the way up, as the elevator stopped at several floors, a man turned to me and asked why I didn’t use my card to go through the turnstile. I pointed to my big computer bag and said that I didn’t feel like looking through there to find it. He laughed and started talking to his buddies about the fight on television the night before.So add confidence to that list. It’s shocking what you can get away with when you expect someone to believe you.
Getting What You Came For
In the end, it’s all moot if you don’t demonstrate that a security breach can lead to a compromise. This can be plugging a small device into the network so that you can later gain remote access, it can be photographing private documents found on desks and in file cabinets, and it can even be accessing employee computers that are left unattended. I already mentioned in passing that I have had opportunities to install devices on networks and to access computers on some of the engagements I’ve done, but there’s more!Hospitals often hire us because they have a lot of private information and critical equipment to protect while also often allowing many people through their doors daily. They walk a fine line of being kind to patients and their families while still protecting patient rights by guarding their security. At one busy hospital, I was set on getting access to the files in the Medical Records room. I tried in a doctor’s coat and in scrubs and didn’t make it past reception. I went back in jeans and told them I was from IT to fix a computer. The receptionist let me in without another word. I opened file cabinets and took photos of the papers inside.At another hospital, I walked up to a reception desk that blocked my way to a cancer center. I told the receptionist that I was from IT and had to manually install updates using a USB drive because the automatic security updates were failing. Not wanting to miss a security update, she let me into the locked area behind her and told me to take my time. She left me alone to install payloads to open remote sessions on several machines and photograph patient records that were lying on desks.On one job I had been hired for had an SE engagement and an internal penetration test combined. This is a great idea because it demonstrates how a real attacker might put the pieces together to gain more access. From the penetration test, I already knew of administrative interfaces on the internal network that allowed default credentials. With my SE hat on, I walked into one of the hospital’s specialty buildings. This is where they treated cancer patients and other patients who would be back for multiple visits. There was a very nice room, open to anyone, off the lobby. Computers were provided to allow patients, friends and family to research what they had heard from their doctors. I sat down at one of these computers and proceeded to login to the internal admin websites that were all accessible from those public computers. In this way, I, or an attacker, could access and change administrative controls for the hospitals systems.
Getting Out
When we perform physical SE jobs for our Raxis customers, we discuss carefully with the customer to discover what they want us to test and not to surpass those bounds. The customers provide us with a “get out of jail free” letter that we use if we are caught. The letter is on the company’s letterhead and provides information about who to call to verify the testing in the event that we are challenged by a vigilant employee. With this, we can boldly enter company buildings without fear of arrest. True attackers will likely not be as careful as we are in our testing… their goal is to get in, get what they came for and then to get out without being caught, whether they cause other harm or not.Once, at a small insurance office, I had gained access to everything that was in scope, but I still had extra time. I had done it all by staying under the radar the first time, so I went back a second time and tried to talk my way into gaining the same access again so that I could see if the people I spoke to would allow me to have access or would stop me. Kudos to them for not believing my story about performing an audit without calling first. Unfortunately, they did not want to be mean to me, so they placed me in a conference room alone for ten minutes while they attempted to reach someone for confirmation. Because I wanted to test them thoroughly, I stayed and eventually handed them my “get out of jail free” letter. If I had wanted to leave, I could have left the building before they checked on me.Then there was the time that I was in a hospital’s administrative building attempting to gain access to Human Resources. I had already spent time in the hospital itself and read a free hospital newspaper that mentioned three star employees by name and with photos. One was in HR, so I went over to the HR building and told the receptionist that the star employee had told me I could wait in their conference room so I could work until my flight arrived. The receptionist happily took me right over to see this star employee. She looked me in the face and told me that she had never seen me before. Since I had nothing to lose, I told her that we had only met twice and I was sorry that she didn’t remember me. I didn’t offer to leave. I stood next to the receptionist and just stared after that. My target told me that she had never met me but that I could stay in the conference room anyway. I stayed long enough to plug a device into the network and then walked out telling everyone that I got an earlier flight. Sometimes the best way to be able to get out is to act like you are comfortable staying… as if you belong there so fully that you have nothing to hide.In my SE career, I have only been forced to show my “get out of jail free” letter once (without me forcing the situation into that). This was an example of an employee doing everything right. I had discovered that a high level manager at the small firm we were tasked with assessing, as well as his wife, had public Facebook profiles. I learned all about them, bought a cake that said “Congratulations, Dad!” and walked up to the receptionist saying that I was his daughter in town to surprise him for his anniversary (which happened to be coming up according to Facebook). I knew my mother’s name and my siblings names, and I had a whole story set up. It was enough to get me into his office, but the receptionist called his assistant to escort me, and the assistant didn’t take her eyes off me. When I tried to catch a coy photo of a paper on my target’s desk, she entered the room and told me that she was calling security. After a brief attempt to talk my way out of it, she stood her ground. Upon receiving my letter, she called the people on the letter to verify that the letter was true. While a lot of these stories make this sound easy, this was an example of a situation where a real attacker could have ended up talking to the police. And it shows what diligence from employees can do to protect the company.
What You Can Do
Hopefully this article was a fun read, and hopefully it scared you a little as well. When someone wants something from your company, they can be very convincing, but you don’t have to be an unwitting accomplice. What can you do?
- Many companies have physical security policies. Ask what yours is. It likely includes several of the following items as well.
- Don’t allow people to tailgate behind you. If a door is locked or protected in some way, let people unlock the door themselves. If they complain, explain that it’s company policy (if it’s not it should be!) and tell them where they can go to sign in and gain access if they don’t have the key or badge needed at your door.
- If you see people you don’t recognize in your internal office space, ask who they are. Ask to see a visitor badge if your company provides those. Many visitor badges have blurry photos and small “approved for” dates. Check the badge closely.
- If you find someone to be suspicious and don’t want to or don’t know how to confront them, call security. That’s what they’re there for. Tell them as much information as you can and keep an eye on the suspicious person until they arrive if possible.
- Keep private and critical documents in locked drawers. Don’t leave them on desks or in unlocked cabinets. Remove these documents from printers and fax machines as quickly as possible as well.
- Let your IT department know of any network ports that are not being used. If an attacker plugs a malicious device into a network port that IT has turned off, you’ve thwarted their remote access to your company’s network.
While this is my last post in this Social Engineering series for now, we’re always happy to discuss what Raxis can do to help you improve your company’s security in this area. You can find more information at https://raxis.com/redteam/social-engineering, or drop us a line at https://raxis.com/company/contact.I’ve heard a rumor that my colleague, Brian Tant, is working on a related blog post about Neuro-Linguistic Programming (NLP) using cognitive resets, visual cues, and body language. Keep an eye out at the Raxis blog for that coming up soon!
Want to learn more? Take a look at the first part of our Social Engineering discussion.