Web Application Penetration Testing
Uncover Application Security Vulnerabilities Missed During Development
Let’s Work Together to Uncover Hidden Security Risks
Web Application Penetration Testing powered by Raxis Strike is different from standard penetration tests due to its focused scope on application-specific vulnerabilities, business logic flaws, and complex user interactions within web-based systems. This specialized approach involves in-depth examination of application functionality, authenticated testing across various user roles, and continuous assessment of critical processes and frequent updates, providing a more comprehensive evaluation of web application security than broader network-based penetration tests.
OWASP Top 10
The OWASP Top Ten is a widely recognized standard for current critical security risks to web applications. Your development team likely uses the list to inform their security decisions, and the controls are embedded in our web application penetration test processes as well. From broken access controls to insecure design and injection vulnerabilities, you can rest assured that our engineers are versed in them all.
Find Business Logic Flaws
A business logic flaw is a vulnerability that arises when an application’s legitimate processing flow can be manipulated to produce unintended negative consequences for the organization. These flaws often stem from flawed assumptions about user behavior or inadequate validation of user input, allowing attackers to bypass security controls and exploit the application’s functionality in unexpected ways.
Validate Security Controls
Your dev team has the responsibility for the entire app – from user experience to security. Your application must validate that all users have authenticated correctly and are authorized to use the proper areas of the application. But security doesn’t end there. The application code must follow proper security procedures to keep data safe. Your developers deal with a lot of moving pieces..
A Different Perspective
Instead of looking at your application as a credible user would, they take a hacker’s point of view, attempting to exploit business logic vulnerabilities as well as code and configuration issues. Raxis gives your development team useful, actionable feedback to give them to tools they need to secure your application.
Comprehensive Role-Based Testing
Cross-Customer Users
Software as a Service (SaaS) customers often require testing to validate that the customers who use the web application are not able to access other customers’ data. Raxis pentesters look for vulnerabilities that could allow these flaws and work to exploit them.
Restricted User
Raxis performs comprehensive application testing on forms, fields, and services throughout the application using all user roles. Testing as a user with limited permissions makes it possible for our engineers to attempt operations that should only be accessible to higher level users.
Unauthenticated User
We hunt for flaws in the login process as well as authentication bypass techniques such as SQL injection, cross-site scripting, and session fixation. Anything from user enumeration and brute-force attacks to direct object references are considered in-scope.
Administrative User
Once logged in, Raxis maps out the application, looking for technical vulnerabilities as well as business logic gaps and flaws. Configuration issues, client-side processing, and session issues are just a few of the areas your engineer will test from within your application.
Two Approaches For Web Applications
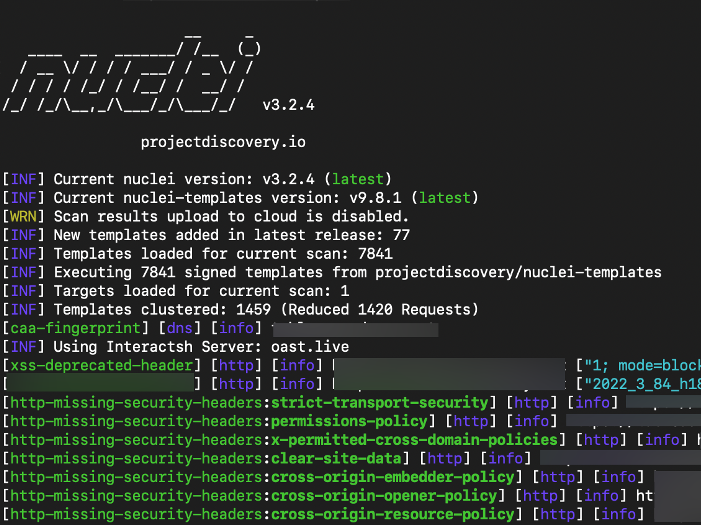
Raxis Strike: Static Penetration Testing for New Applications
Raxis can test your application in a QA environment before you go live so that you — and your customers — can rest assured that security features have been thoroughly tested and protections are in place to stop malicious actors from gaining access to your site and systems or even disrupting the environment.
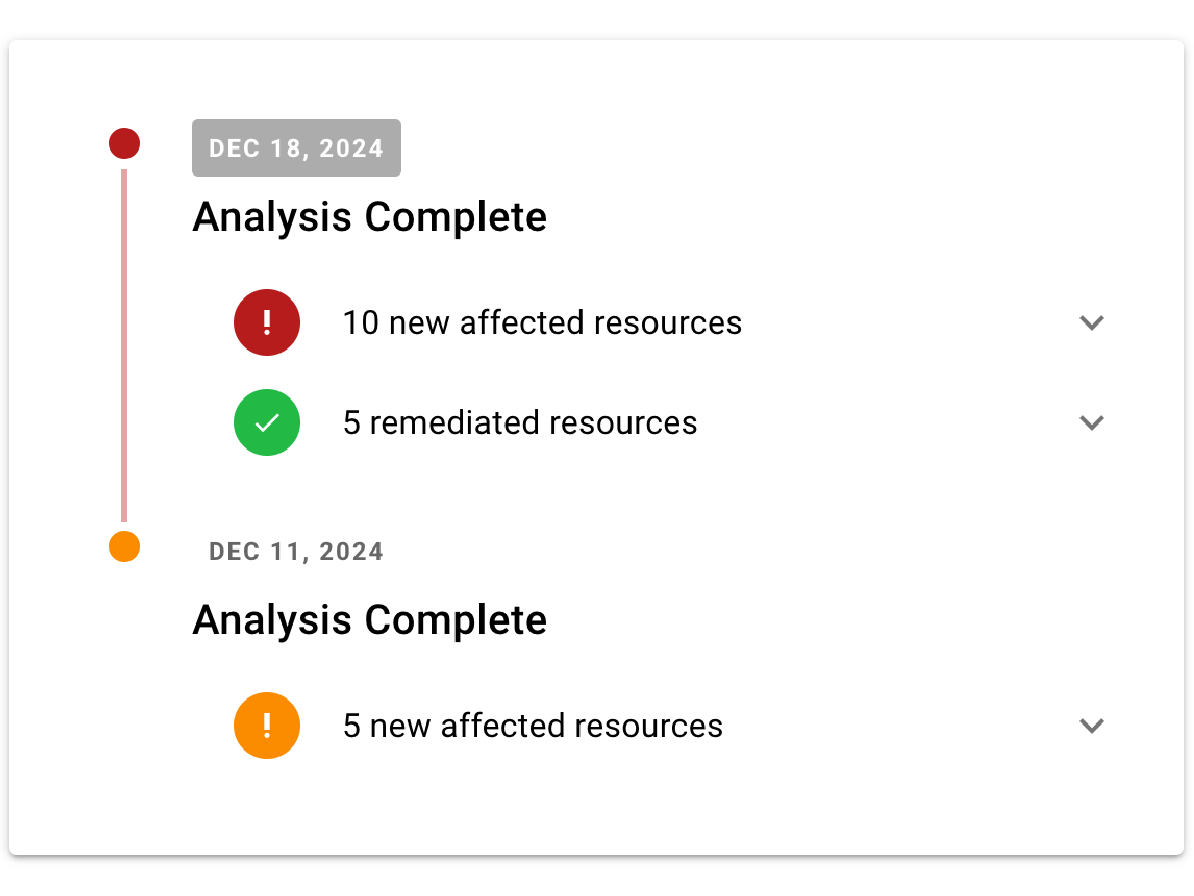
Raxis Attack: PTaaS for Continuous Development
When your application changes rapidly with agile teams pushing updates to production often, Raxis recommends PTaaS for web applications. This service includes unlimited, on-demand testing, allowing your security to keep up with your constantly changing application.
Common Web Application Vulnerabilities
By simulating real-world attacks, Raxis Strike Web Application Penetration Testing uncovers hidden weaknesses in web applications, including injection flaws, authentication vulnerabilities, and misconfigurations, allowing organizations to proactively strengthen their security posture and ensure compliance with industry regulations.
Broken Access Control
This vulnerability occurs when access restrictions are not properly enforced, allowing attackers to bypass authorization and perform unauthorized actions or access sensitive data. It’s the most prevalent vulnerability according to recent OWASP rankings.
Injection Flaws
These vulnerabilities, including SQL injection and cross-site scripting (XSS), allow attackers to insert malicious code into applications. SQL injection targets databases, while XSS enables attackers to inject malicious scripts that execute in users’ browsers.
Cryptographic Failures
Previously known as “Sensitive Data Exposure,” this category involves vulnerabilities related to inadequate protection of sensitive information, often due to weak or improper cryptographic practices.
Insecure Design
Insecure design refers to flaws or weaknesses in a software system’s architecture, design, or logic that can be exploited by malicious actors, often resulting from a lack of security considerations during the early stages of development.
Security Misconfigurations
These vulnerabilities arise from improperly configured application settings, default accounts, or exposed error messages that reveal sensitive information.
Cross-Site Request Forgery (CSRF)
CSRF attacks trick users into performing unintended actions on a web application where they’re authenticated.
Server-Side Request Forgery (SSRF)
Server-Side Request Forgery (SSRF) is a web security vulnerability that allows an attacker to induce the server-side application to make HTTP requests to an arbitrary domain of the attacker’s choosing.
Authentication Failures
This vulnerability allows attackers to make the server perform unintended requests, potentially bypassing security controls.
Business Logic Errors
Business logic errors are vulnerabilities that arise when an application’s legitimate processing flow can be manipulated to produce unintended negative consequences for the organization.
Cross-site Scripting Explained
Cross-site scripting, or XSS, is a common vulnerability found on web application penetration tests and is often misunderstood.
